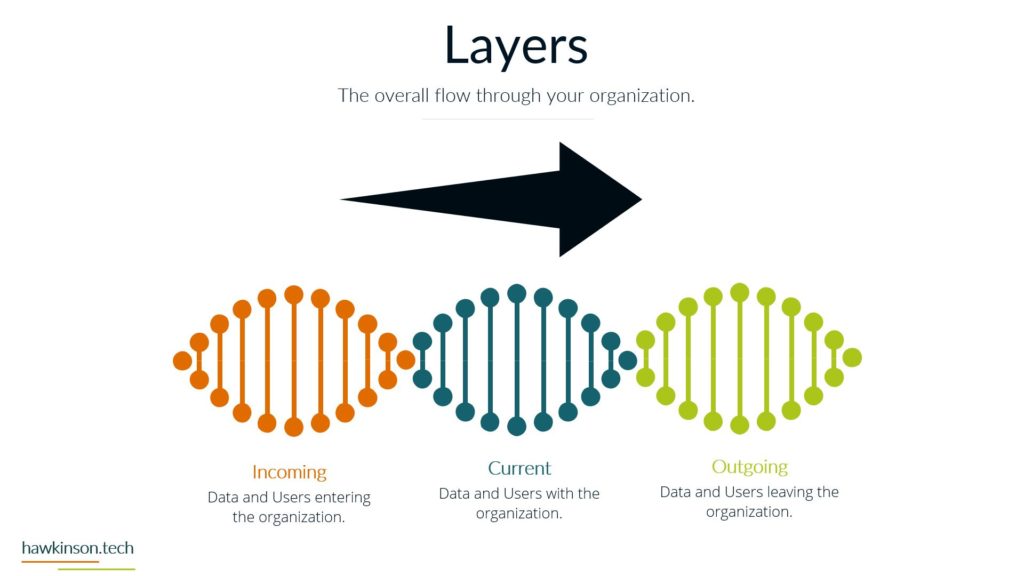
The Crucial Role of Data Security in the Digital Experience
In the fast-paced world of digital experiences, data security is indispensable for businesses striving to protect sensitive information and maintain a seamless online environment. This comprehensive article will delve into the various facets of data security and explore its crucial role in shaping a robust foundation for the digital experience. Discover how safeguarding data and implementing robust security measures can enhance your organization’s digital presence and protect against potential threats in the ever-evolving digital landscape.
The Human Factor: Addressing Data Security Risks from Within
In the digital age, businesses rely heavily on technology, but the biggest security threat often comes from an unforeseen source – their own people. Employees and stakeholders with access to valuable data may inadvertently or maliciously compromise its security. Social engineering tactics, phishing attempts, and exploiting human vulnerabilities are important to understand.
Social engineering is manipulating individuals to divulge confidential information or perform specific actions. It is one of the most significant data security threats and occurs online and offline. For example, attackers might call employees pretending to be from the IT department and ask for their login credentials or send phishing emails to trick users into clicking malicious links or sharing sensitive information. To mitigate these risks, organizations must build a security-conscious culture that educates employees about potential threats and encourages them to be vigilant.
Fortifying Your Digital Fortress: Strengthening Software Security
While people are a significant security threat, software security is equally critical. The software used in an organization plays a pivotal role in safeguarding data and digital experiences.
Access control is essential to prevent unauthorized individuals from accessing sensitive data. Businesses can limit data exposure and potential breaches by defining user permissions and access levels. Properly managing access privileges ensures that users only have access to the specific information and functionalities they need to perform their roles.
Additionally, software updates are vital in maintaining data security. Regular updates patch known vulnerabilities and protect systems from emerging threats. Outdated or legacy software can have security flaws that malicious actors can exploit. Organizations can significantly reduce the risk of data breaches by staying up-to-date with software patches and security protocols.
Setting the Boundaries: Establishing Data Security Policies
Organizations need to establish clear and comprehensive data security policies to build a strong foundation for data security. These policies define the rules and procedures for data access, password management, and device usage.
Password management is a crucial aspect of data security. Weak passwords make it easier for attackers to gain unauthorized access to sensitive data. Encouraging employees to use strong, unique passwords for each account and implementing multi-factor authentication can bolster data protection significantly.
Device usage policies are also essential, especially with the increasing prevalence of remote work. Employees often use personal devices to access company data, creating potential security risks. Organizations can ensure that sensitive information remains protected, even when accessed from remote locations, by implementing policies that define device usage guidelines and security measures.
Beyond Digital: Bolstering Physical Data Security
Data security is not limited to virtual realms; it extends to the physical environment. Protecting physical locations that house sensitive data is critical to maintaining a secure digital experience foundation.
Access control systems, such as key cards or biometric authentication, help prevent unauthorized access to sensitive areas within the organization. Visitor management protocols ensure that only authorized personnel can enter designated spaces.
Physical security extends beyond the office walls. External environments, such as data centers or cloud server locations, must also adhere to strict security measures. Data centers should have robust access control, surveillance, and monitoring systems to prevent unauthorized entry and protect the servers that store valuable data.
Protecting Data Beyond Office Walls: Strategies for External Data Security
Securing data outside the office becomes imperative with the rise of remote work and mobile access. Employees often access company systems from external environments, such as public Wi-Fi networks, increasing the risk of data breaches.
Organizations can implement Virtual Private Networks (VPNs) to encrypt data transmitted over public networks to protect data in external environments. VPNs create a secure tunnel that shields data from potential eavesdroppers.
Mobile device management (MDM) solutions are crucial for securing data on employees’ mobile devices. MDM allows organizations to remotely manage and secure devices, ensuring that sensitive data remains protected, even if the device is lost or stolen.
Finding Harmony: Balancing Data Accessibility and Security
Achieving a seamless digital experience requires striking a delicate balance between data accessibility and security. Organizations must provide stakeholders with the necessary information while maintaining stringent security protocols.
Role-based access control (RBAC) is an effective way to achieve this balance. RBAC allows organizations to assign specific roles to users and grant them access to relevant data and functionalities. Organizations can minimize the risk of unauthorized data exposure by tailoring data access to specific roles.
Personalized data dashboards also contribute to a better digital experience. Stakeholders can access relevant data quickly, enhancing productivity while minimizing potential security risks. Employing data visualization techniques can simplify data interpretation, making it easier for stakeholders to understand and use data securely.
Empowering the Guardians: Educating Users on Data Security
User education and training serve as the first line of defense against data breaches. A well-informed workforce maintains data security and ensures a seamless digital experience.
Organizations should conduct regular security awareness training programs for employees and stakeholders. These programs should cover common security threats, phishing awareness, data protection best practices, and the importance of adhering to data security policies.
Simulated phishing exercises can help employees recognize and resist phishing attempts. These exercises create a safe environment where employees can practice identifying suspicious emails and reporting them to the appropriate IT personnel.
The Future of Data Security: Nurturing a Resilient Digital Experience Foundation
Data security forms the bedrock of a robust digital experience foundation. Understanding the risks posed by internal and external actors, prioritizing software security, implementing comprehensive policies, and recognizing the significance of physical security measures create a holistic approach to safeguarding data. By embracing these strategies, businesses can foster a secure digital environment, enhance the overall digital experience, and fortify themselves against potential threats in the ever-evolving digital landscape.
Data security remains an ongoing effort in the dynamic world of digital experiences. Continued vigilance, regular assessments, and updates to security protocols are necessary to adapt to new threats and ensure that the organization’s digital experience foundation remains resilient. By continually striving for excellence in data security, businesses can provide their stakeholders with a seamless, secure, and exceptional digital journey.