Digital Experience | Pillar 1 Stakeholders | Lesson 3 Devices
Follow Me Elsewhere:
Play Video
Play Video
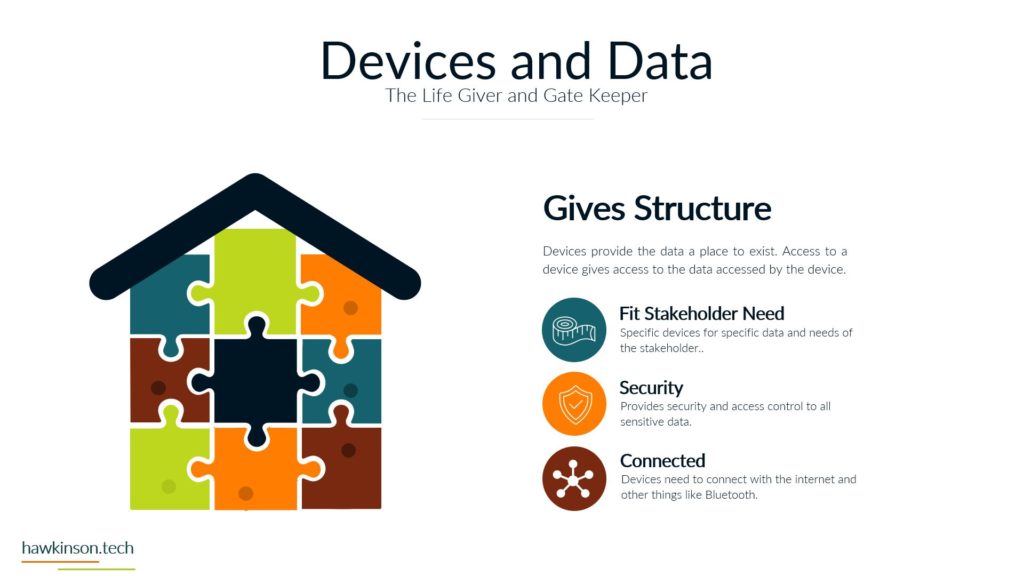
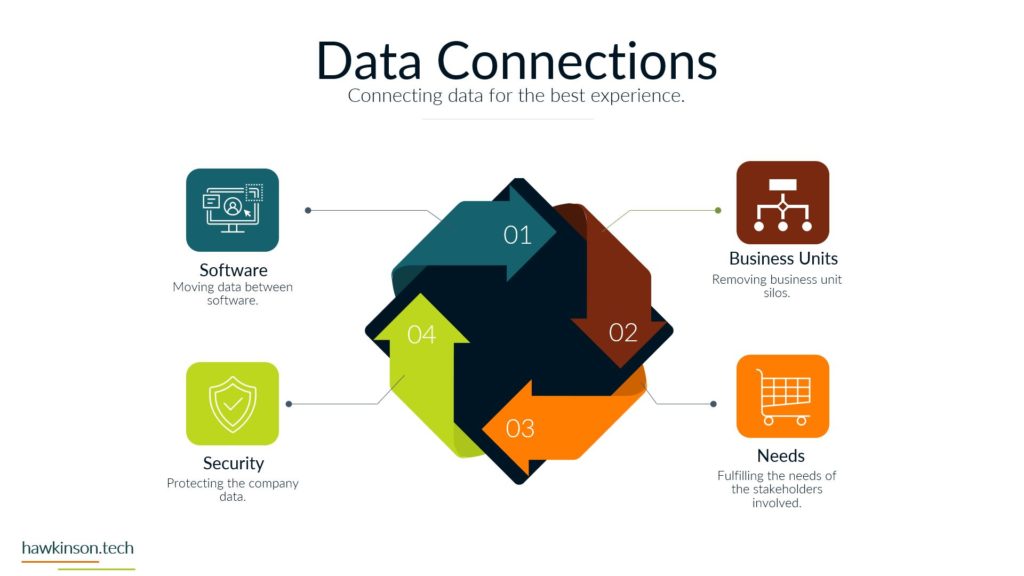
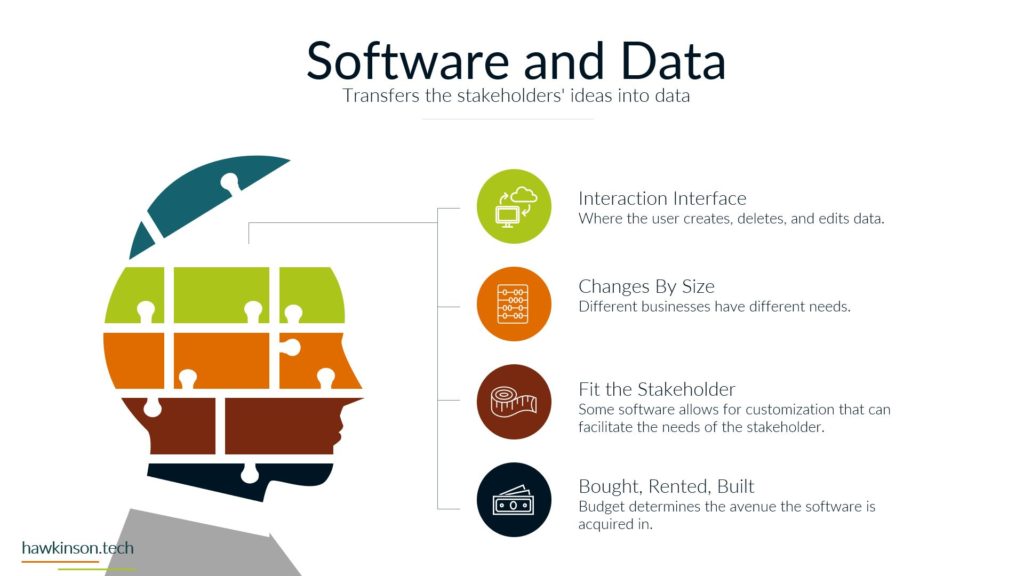
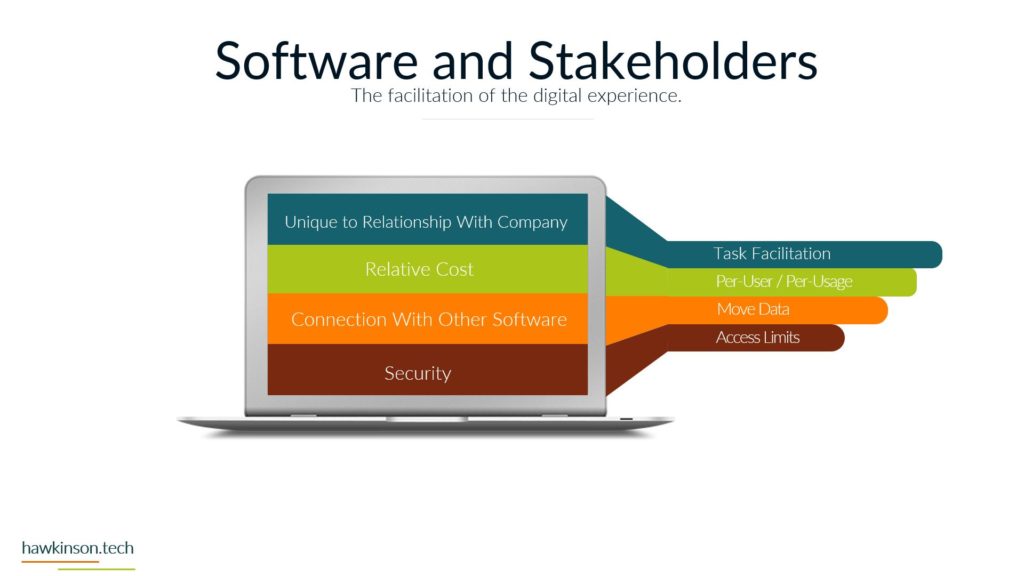
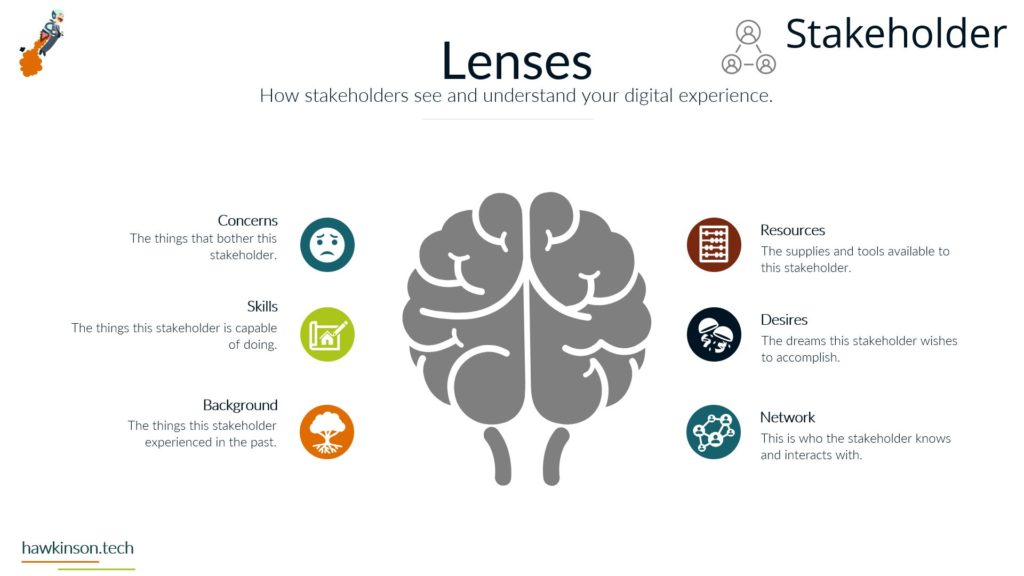
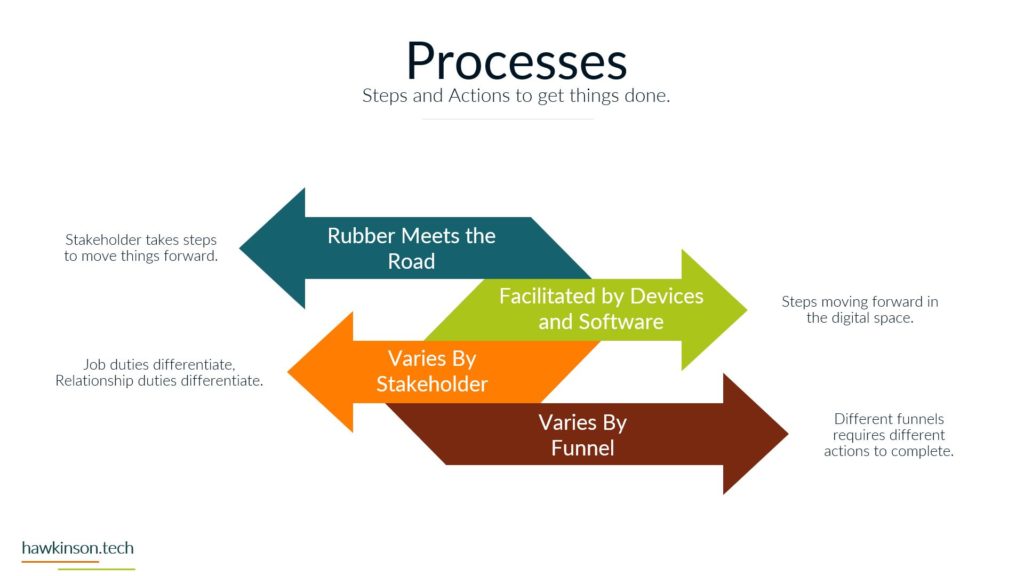
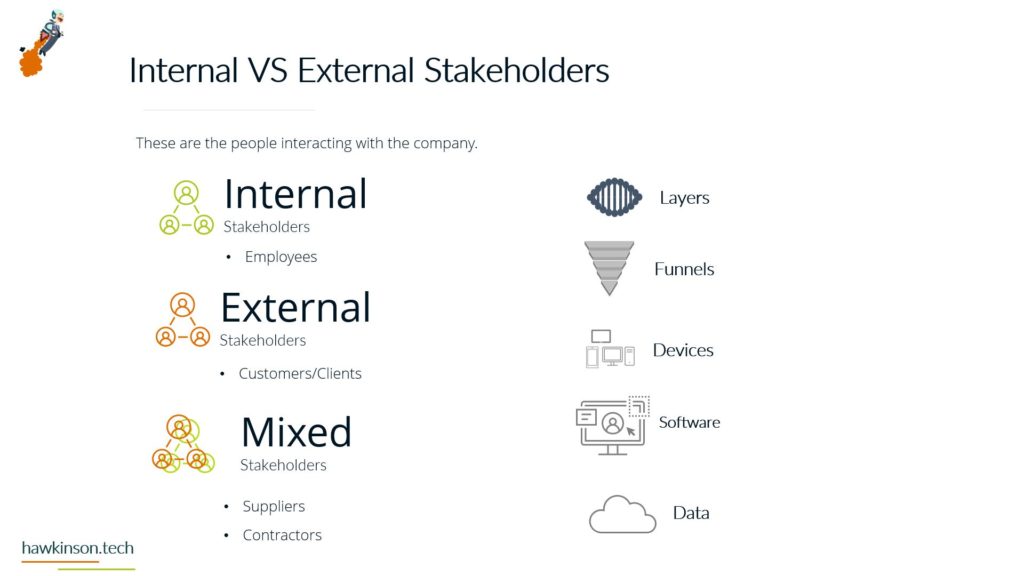
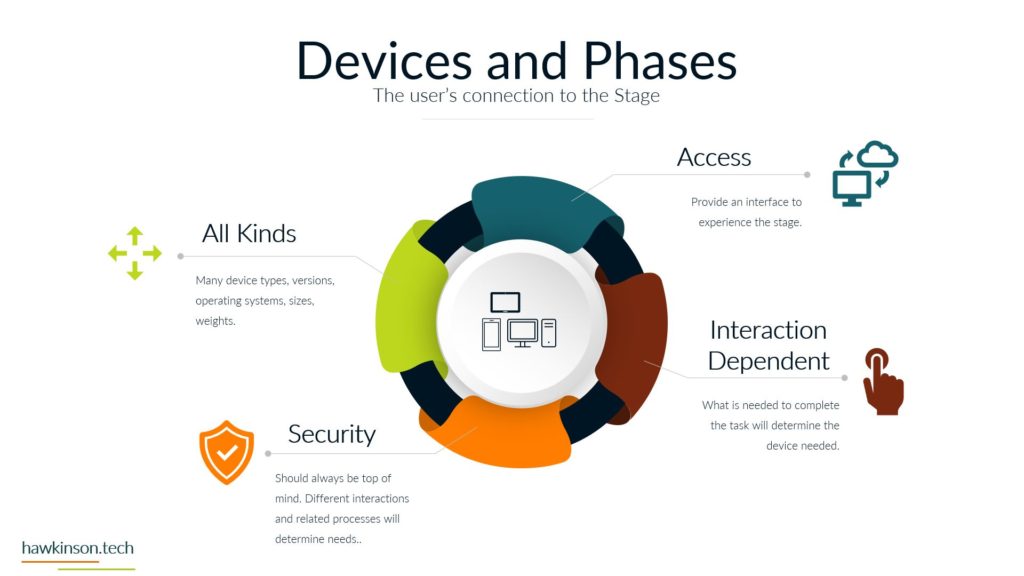
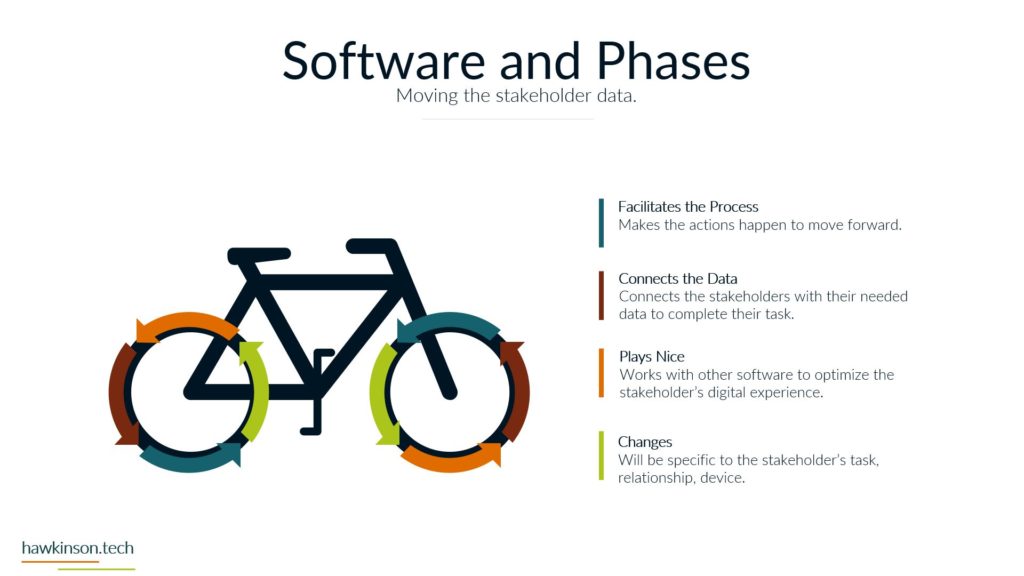
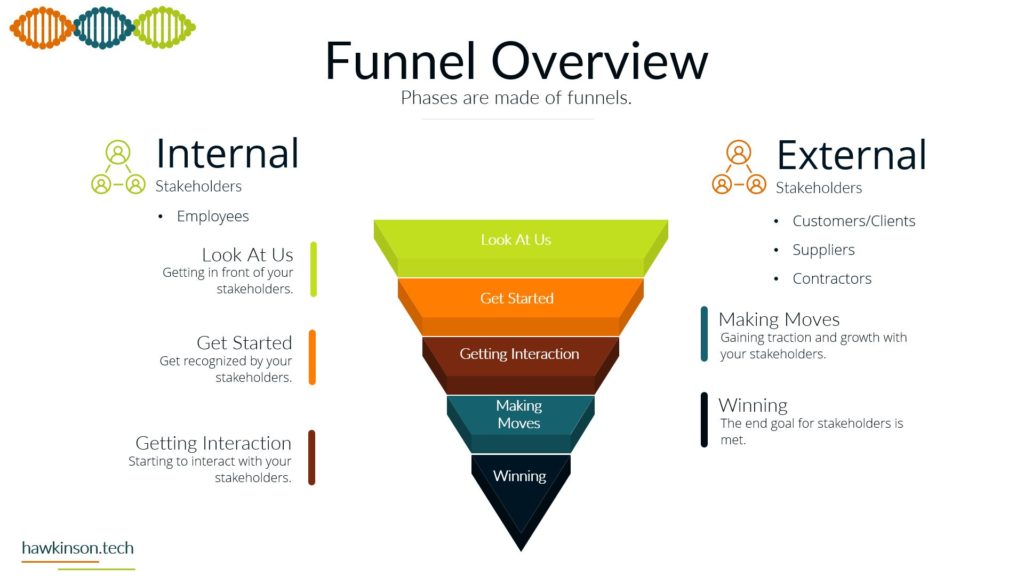
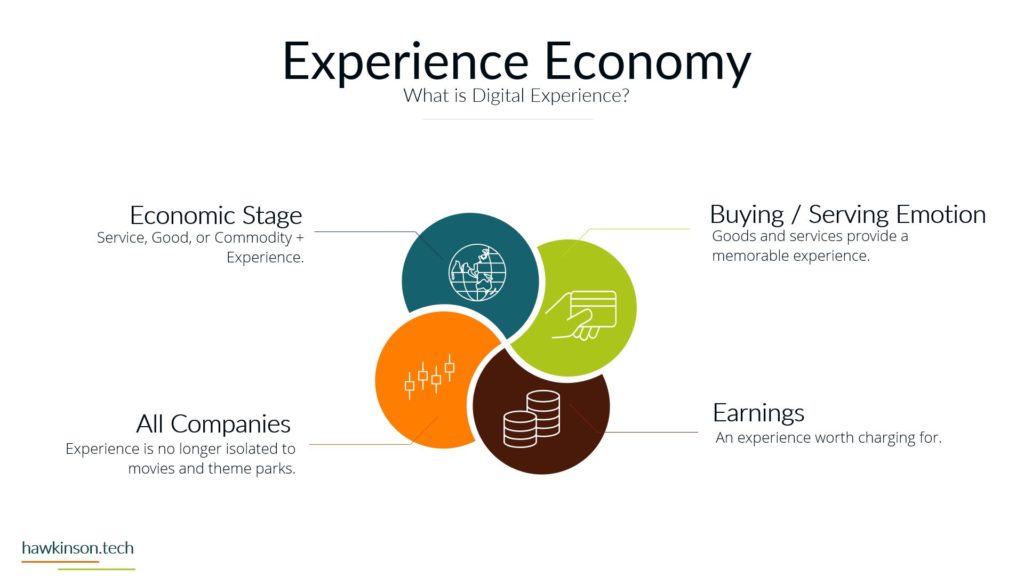
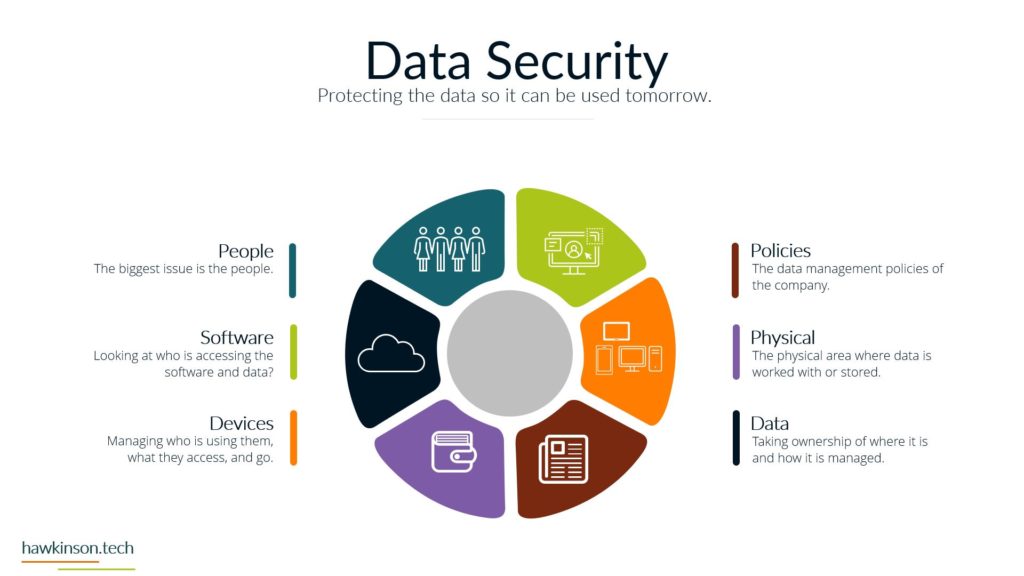
Alright, so let’s dive into some of the different devices and what we have with our expectations with the stakeholders and the devices that they’re using. So when it comes to devices and our digital experience, we need to be aware that internal and external stakeholders have different devices. And what I mean by that is we’re going to have different ways of regulating the devices. We might have different devices that they use to interface with the companies data and the things that they do in order to fulfill their requirements with the company. So let’s take a look at kind of just just different devices in general. So different devices provide different types of experiences and we’ll get very in-depth. In this here later in the course. But for now, just know that the experience that somebody has on a desktop device is going to be vastly different than a phone or a tablet, just because of the way that the interfaces work. I mean, if you’ve looked at any app and experience, they’re on a website or on an app, you’ll know that they’re very different. And then from there it gets even more different if we’re looking at VR devices or types of artificial. Realities and the way that those work with different stakeholders, it’s a very different set of experiences. You know, we’re working at some sort of fictitious 3D World or some sort of overlay of digital on top of a real world experience that we’re looking at some of like the VR or the AR capabilities. And then if we’re looking at just kind of very basic devices that can be used for people with special needs, then we get into things, you know, like our screen. Leaders or eye trackers or TTY devices where we get different ways of just working with a website and app or some sort of piece of data. So when we’re working and producing this internally with internal stakeholders and have a bit more of a neutral stance, mostly because if we’re providing the companies devices then we have a lot of control over those devices and what goes on. So we do want to. Be concerned, but we can set up things in place to make it so we can manage these devices and be able to foster them for the best result for that particular stakeholder. Now with external stakeholders and different devices, we do have a lot of concern. We want to make sure that the expectation of what we’re looking to have them do meets the results of the device itself. So for example, if we were doing super complex. Tasks and having them accomplish this on a phone might not be a best fit. Desktops can usually be better kind of devices for very complex situations. Likewise with external users. If somebody was bringing like a screen reader to work with our website, we want to make sure that we’re encompassing that. What I’m getting at, and the reason for the high concern with external stakeholders is we don’t have a lot of control as to what they’re bringing. For the most part, we don’t really even know what it is until it actually. 1st to unfold. So we want to make sure that we’re just very concerned about what they’re bringing to the table. For mixed stakeholders, this might not be as big of a concern because suppliers might not be as kind of the relationship might be, so might not be as critical on the device interface with the company. However, external stakeholders that are customers and clients could be a vastly different situation. Those customers and clients have expectations and so. If we’re setting them up to go through and work a complex situation, but only providing it to them on the phone, well, then those external stakeholders could frankly just go find somewhere else that is able to fulfill their needs. And that’s where it becomes a high concern. Because we want to make sure that the digital interface that we’re providing to people that we’re selling and trying to move from A to B and provide their desired result that we’re doing it in a way that actually fits their needs and fits their expectations. Now the next one we have is BYOD or bring your own device. This is all about stakeholders that just bring their own device. And this opens up a very interesting situation. So even with internal stakeholders, we want to be very concerned about bringing your own device. The reason for this is an internal stakeholder is more likely to have access or ways of accessing sensitive company data that an external stakeholder may not have access to. And so due to that paradigm in that situation. The internal stakeholder, we want to make sure that we are protecting that information and when they bring their own device, they can get very hairy because the bring your own device can allow for just different devices or different ways of setting up and configuring the device that may allow access into various security parameters or into various documents and data versus when we’re providing the device to them. We’re able to control that when we provide the device because it’s a company owned device, we can go through and set up all kinds of sets of security and parameters on the device to protect it. When they bring their own, that’s literally their own device and so it’s pretty much subject to the user. But even as a company, if you were to have individuals bring in their own cell phones to access company data, when they enroll that device into the company, that means that the company has access into the device. That’s it. As if it was their own device. And for a lot of users, they may not want to put up with that. So they may find ways of getting around the device or the securities. Yes, there’s ways that we can set up security parameters on what they can access, but then that means that them on their own device might not be able to access that information based on the security protocols we have in place. So if we have a bring your own device situation with internal stakeholders. We want to be very aware of what information they’re accessing, what types of concerns we have about them bringing their own device. If we don’t allow them to access it on their own device, what does that do for their experience and being able to fulfill their job duties. And this things that’s interesting though is with external stakeholders it’s a bit more neutral. Not that you shouldn’t be concerned, not that you shouldn’t try to regulate it, it’s more just that the security parameters that are in place. Are likely to not necessarily be noticed by an external stakeholder, mostly because they’re likely not act trying to access that information. If they are, then it’s going to come across as a very clear malicious attempt. You know, if an external stakeholder, whether it be a supplier or a customer, is trying to access super sensitive comfy and company information, then there’s an issue there, there’s something going on and that needs to be addressed. But The thing is, is with all of these external stakeholders. They’re all going to be bringing their own device, so it’s going to be more of a blanket situation where we’re not having to be as granular and concern as to what they’re able to have access to. The other side of it too is an external stakeholder brings their own device to work with the company. We can also go into set up specialized security protocols for that particular user and usually that’s a few one off versus if we have internal users doing it then they can be whole groups of. Users that are in various different situations and require hundreds of very specialized situations that might not be sustainable for the company to take advantage of or be able to kind of sufficiently work through. So I just want to be concerned that when we’re having users bring their own devices and access company data, what we’re allowing them access to and how those security protocols impact their ability to facilitate their job successfully. And their expectations of essentially allowing the company to have access over their whole device just because again when we bring your own device, if we take over that device as the company will effectively the user is paying for something that we’re taking over. And as an internal stakeholder that can also lead to some poor company expectations because then you’re, you know, private cell phone is now monitored by your company. There’s different protocols, share of isolating apps and that kind of stuff, but. Then it can become a concern as to what’s all being shown to the company and what do they have access to. But again, with external stakeholders, it’s kind of to be expected that they’ll be bringing their own device into the experience. And now the third thing we’ll talk about and there’s definitely way more and we’ll get into way more about devices and stakeholders. But software, the software is essentially going to be our, our kind of initiation from connecting the device into the company’s data and being able to. Facilitate that kind of interrelationship there. And so when it comes to our internal stakeholders, this one labeled kind of as neutral just because there’s. People are always going to use software and our internal users are always going to have some sort of software that they’re using, especially in today’s age, whether that’s going to be, you know, a Word document or maybe some proprietary CRM software, they’re going to have access to it. We have different ways that we can go through and mediate access to that software. I guess what I’m looking at here, what I should highlight on is the software can be dependent on the device. For example, a user could have their own cell phone that they bring in to access the software, but likewise they might be able to access that software by just signing into a URL from their own personal computer. And so really what we’re looking at is when it comes to the devices, that the software essentially may stay neutral depending on how users access it. And so there might be other parameters, maybe through other software, that we would look to make this a protection. There are ways we would go through and administer the software to the users, external stakeholders. This is also again gonna stay neutral because external stakeholders were likely providing them the login to that software. We’re likely already setting up security protocols to diminish it, and we’re already knowing that they’re bringing their own device to the situation, so it gives us a much better idea of what to control and how to contain that particular user. Now one thing I do want to highlight here on all of it is nowhere in here did we mention anything with low concern. And the reason is, is because you never want to kind of just freely allow any company data out there. You always want to be concerned about the data users or accessing what stakeholders have access to and how they’re using that data. You want to set things up properly to protect and mitigate any types of damages to that data. So there’s no low concern here because we want to make sure that we’re always protecting data. Essentially, it’s getting so stringent and severe with security protocols and data that even the Department of Defense has told it companies that they need to act as if they were already breached means acting as if somebody already has access to your sensitive information. So we definitely have no low concerns. We always want to be concerned about the company. You know, and as we’ll get into the data section, we’ll look at how important this is to protect. If we’re not protecting data, it could literally mean the end of a company if somebody were to get in and destroy that data. So here’s just a brief overview of our devices and stakeholders and just looking at kind of a comparison of internal stakeholders and some big things to be aware of as we’re administering this digital experience. So next we’ll get in a bit. Deeper into the software itself and our stakeholders and how they work with them.
Related Content
More Content
Cyberattacks and threats are increasing daily, and business must protect their websites and clients by installing the best WordPress security plugins available.
A dependable CRM solution can streamline many tasks of your daily business. Have a look at the must-have features of CRM solutions.
Create a professional and functional website with ease using online page builders. Explore factors like ease of use, customization, features, mobile responsiveness, SEO tools, support, and pricing to choose the right website builder for your needs.
Discover five free tools that will take your email marketing campaigns to the next level. From AI-powered personalization to deliverability tools, these platforms offer features to optimize your email content, improve deliverability, and increase engagement. Whether
Discover how ActiveCampaign’s professionally designed email templates can elevate your email marketing strategy. ActiveCampaign offers the tools to captivate your audience and make a lasting impact, from visually stunning designs to customizable layouts. With responsive designs
Would you like to know what are the critical parts of eCommerce platforms? You can read on to explore the essential factors before buying an eCommerce site.
In this article, we’ll explore the various processes involved in email marketing automation, the tools available to marketers, and the steps to take when choosing the right tool for your business.
Email marketing is a versatile and effective strategy that can be applied across industries to engage customers, drive sales, and build relationships. This article explores the application of email marketing in industries such as retail, healthcare,
Email marketing is one of the mainstays of digital marketing, offering a direct communication line to your customers. Read on for more.
Discover effective examples of email marketing campaigns that enhance engagement and drive conversions. Explore strategies like welcome email series, newsletter campaigns, abandoned cart emails, re-engagement campaigns, personalized recommendations, and seasonal/holiday campaigns. Learn how to nurture relationships,
eLearning has increased in popularity, and the demand for WordPress LMS options is high. Read here to learn about the best options for your eLearning platform.