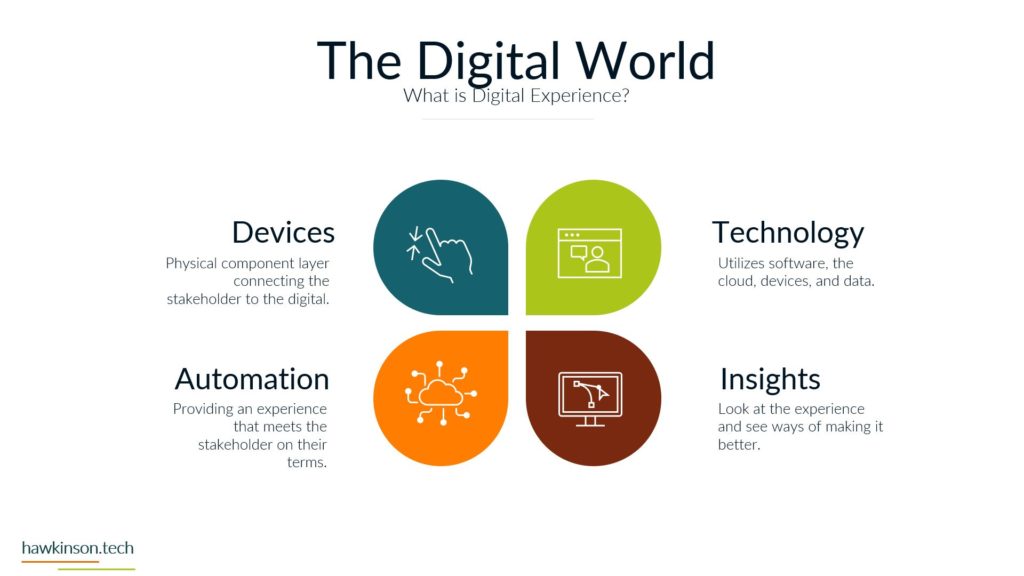
All-in-One WP Security is a comprehensive security plugin for WordPress websites that helps protect your site from online threats and vulnerabilities. The plugin offers an extensive range of features to improve your website’s security and reduce the risk of hacking or unauthorized access.
Here are the key features of All-in-One WP Security:
User Account Security
The plugin provides features to strengthen user account security, such as password strength requirements, username change prevention, and display name obfuscation.
User Login Security
All-in-One WP Security offers login security features like login attempt limits, IP blocking, and customizable lockout durations to protect your website’s admin area from unauthorized logins.
Database Security
The plugin helps protect your website’s database by offering features like database table prefix renaming, scheduled database backups, and database security checks.
File System Security
All-in-One WP Security provides features to protect and monitor your website’s file system, such as file permissions checking, PHP file editing restrictions, and real-time file change detection.
.htaccess and wp-config.php File Protection
The plugin secures your website by configuring and protecting crucial .htaccess and wp-config.php files, which control access to your site and its various directories.