In this video, we explore how data and devices interact in a digital experience.
Digital Experience | Pillar 3 Data | Lesson 2 Data and Devices
Follow Me Elsewhere:
Play Video
Play Video
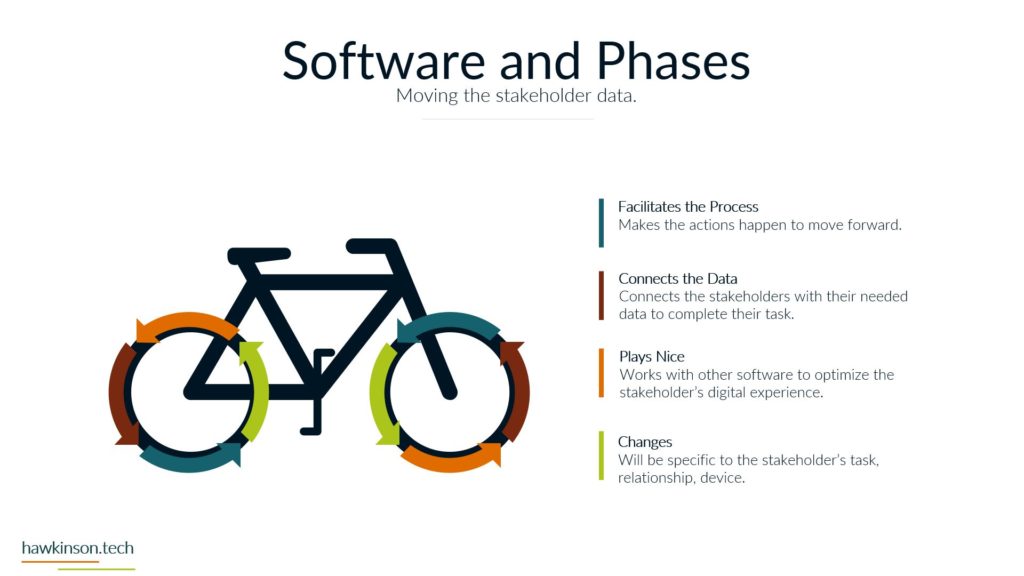
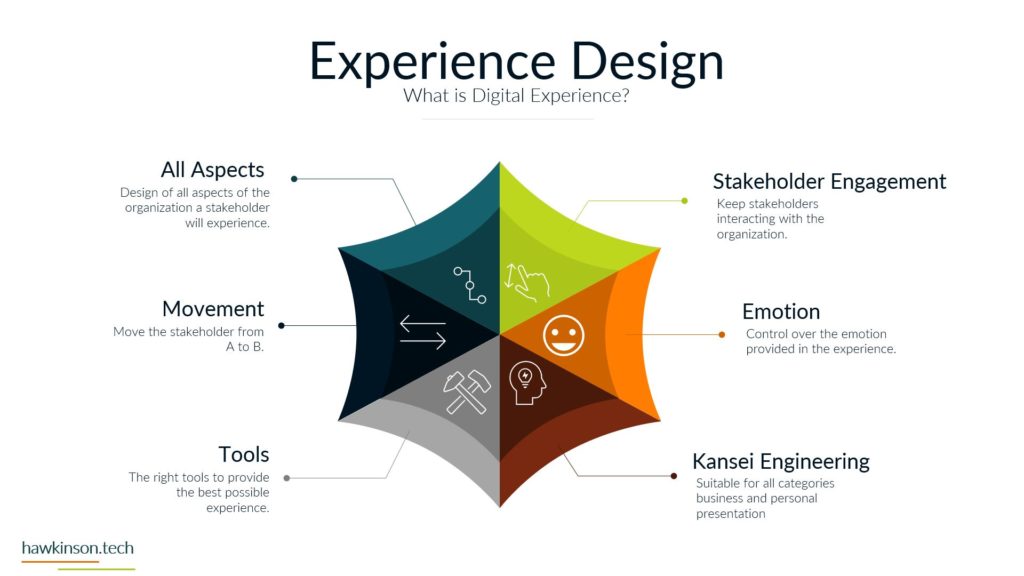
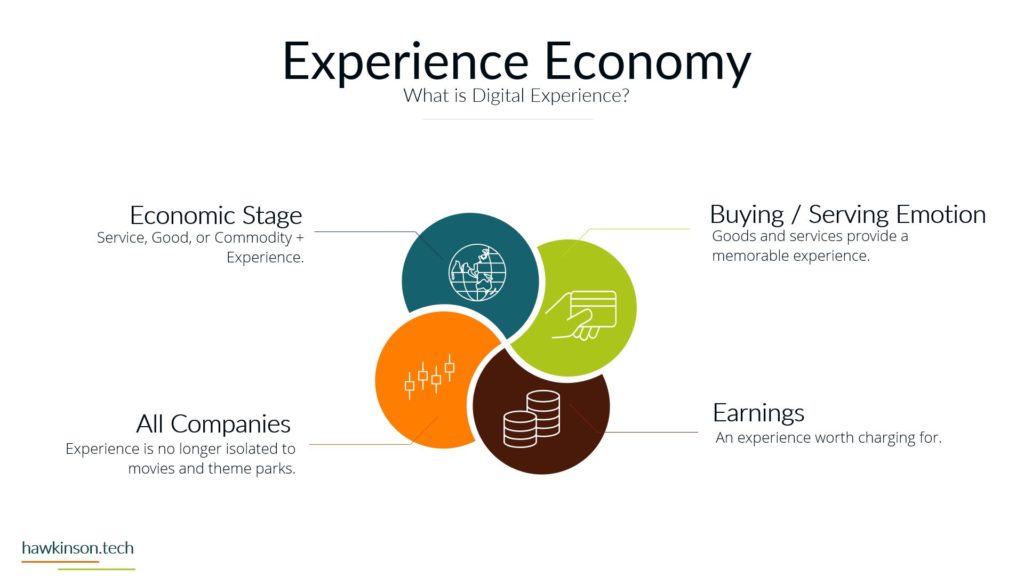
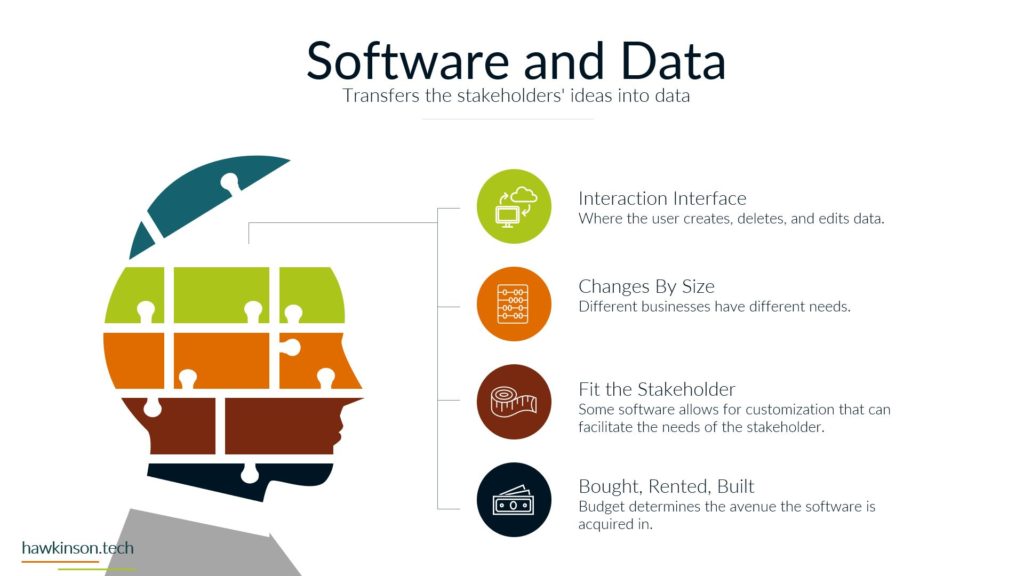
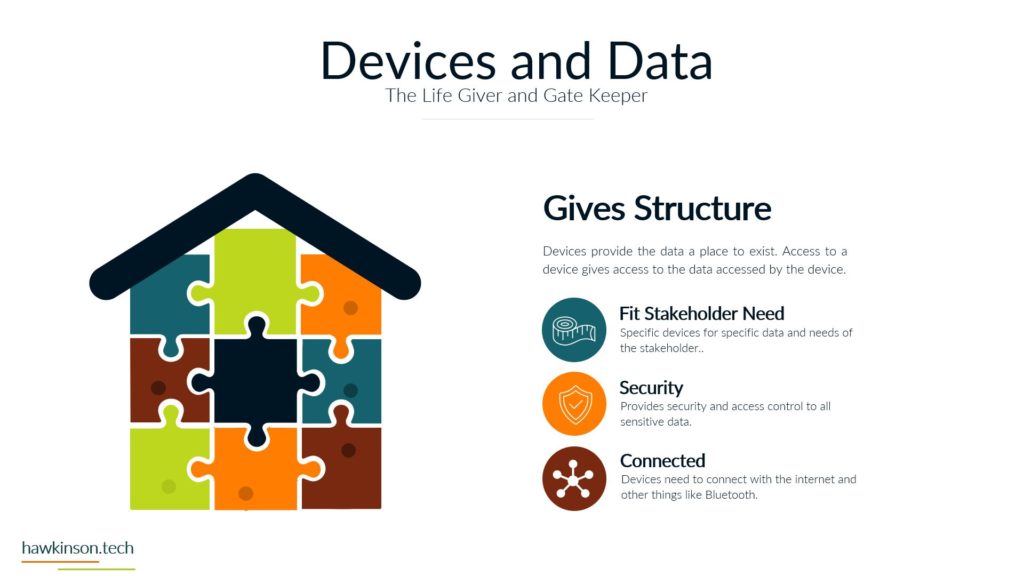
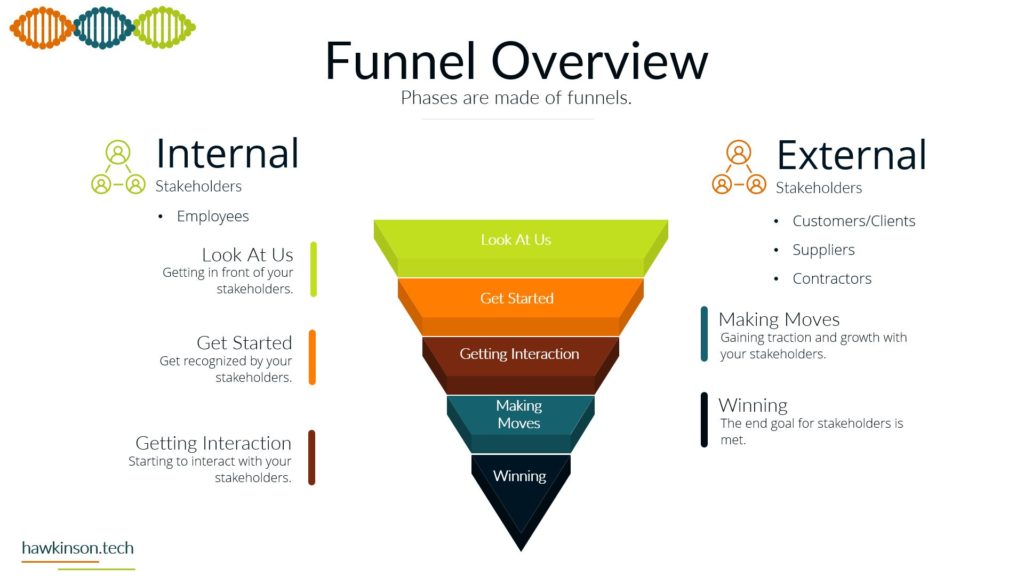
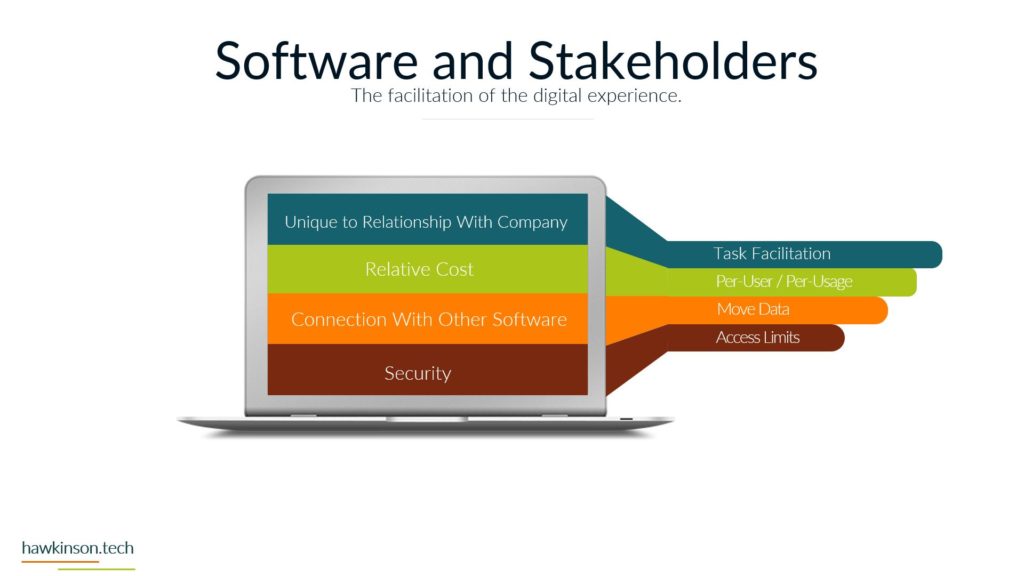
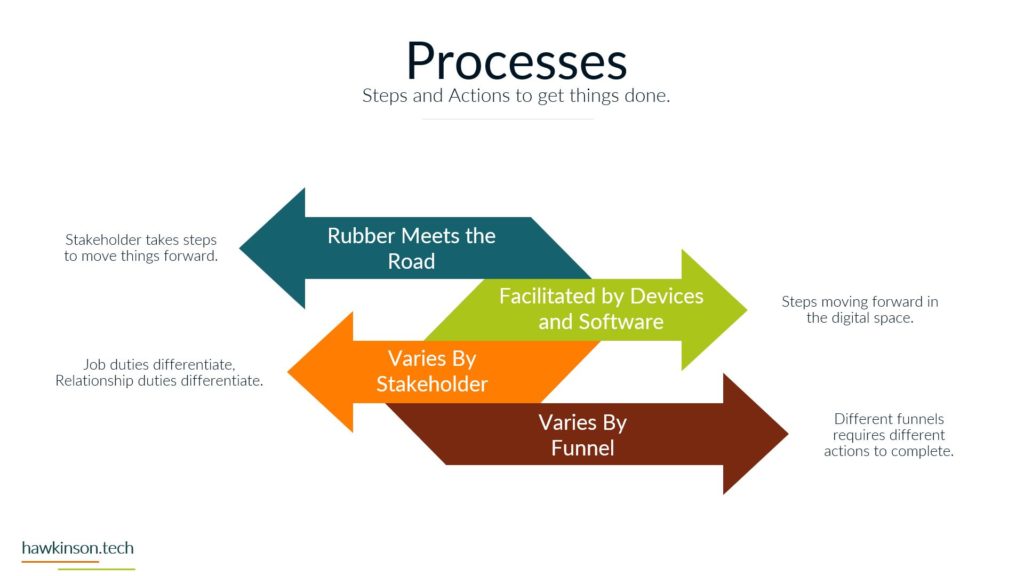
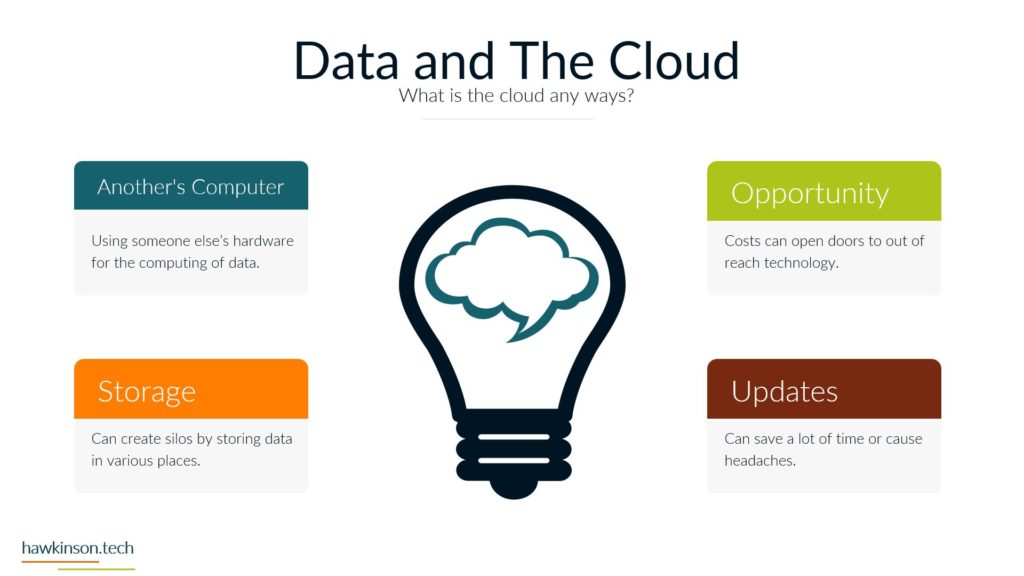
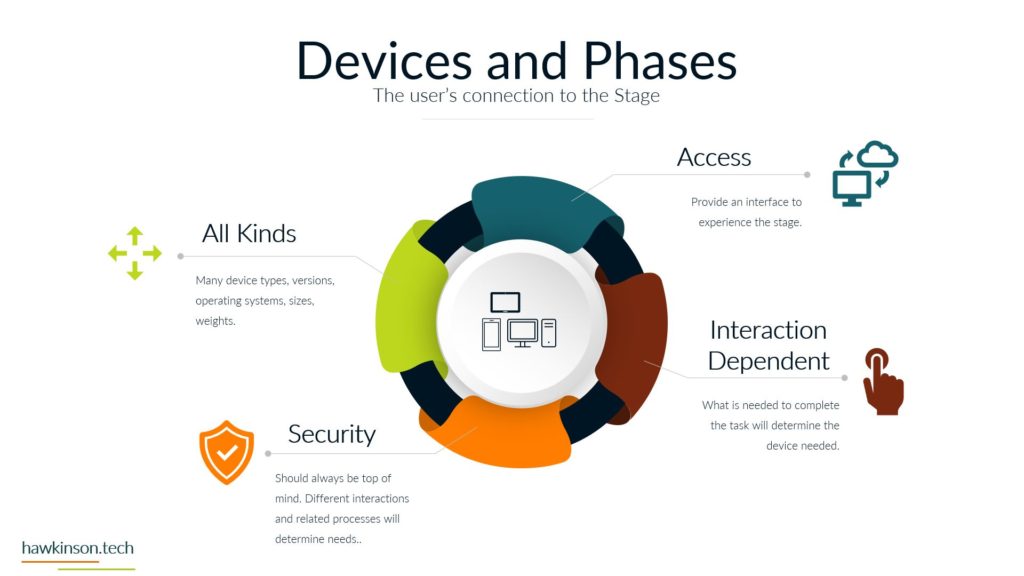
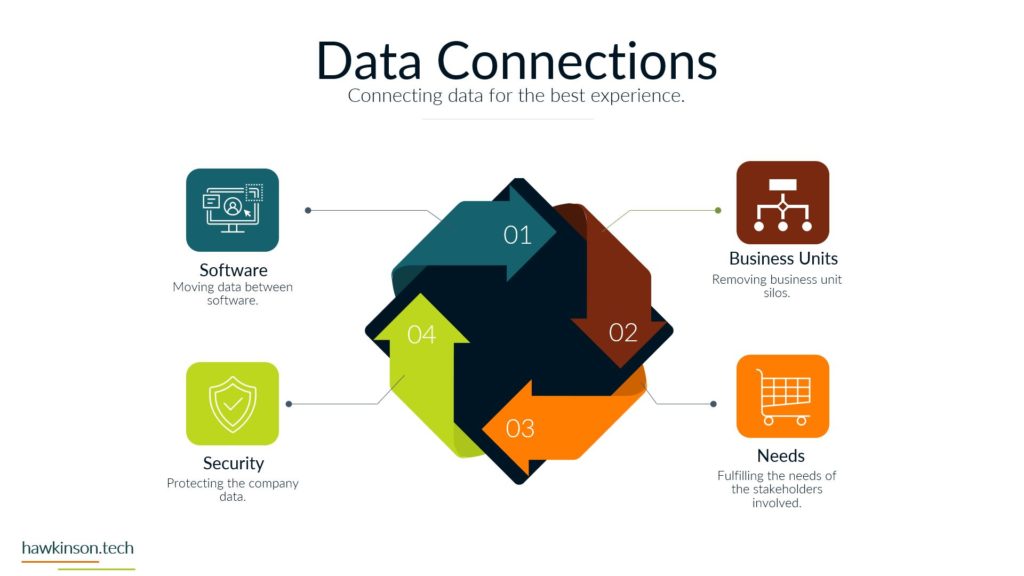
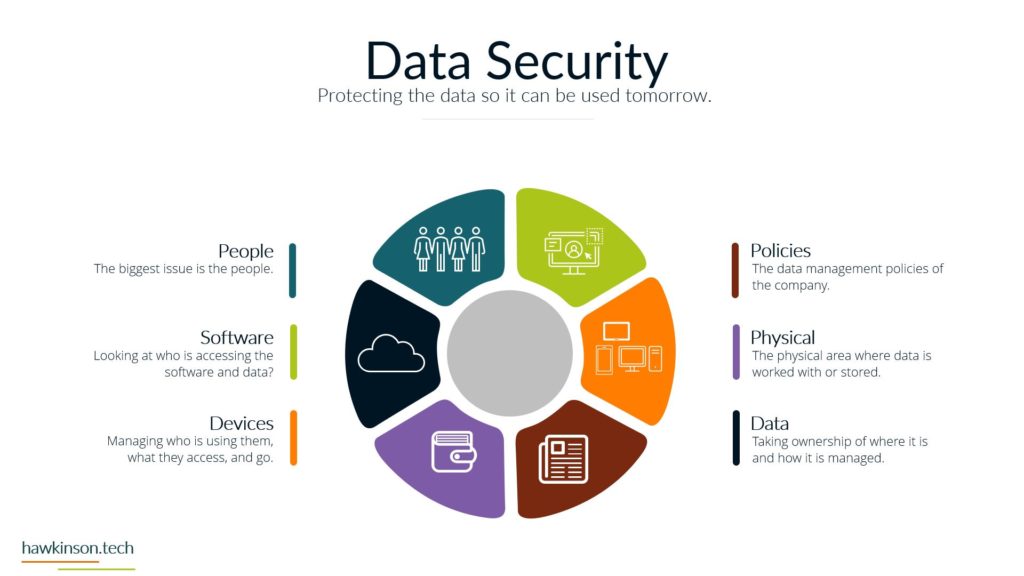
Now let’s take a look at devices and what devices mean for our digital experience. So one way we can look at devices and the data that’s behind them and what they do for the organization is giving it structure. And I bring this up because yes, we’ve talked about software and as an interface it also provides structure, but if we don’t have any. Access Internet software then the software is kind of pointless. So devices give us that ability to access the software which gives the software structure. Different devices and different device types will produce a different experience that can be related to the users. For example, a user on a mobile device is likely to have a different experience than a user on a desktop or a laptop and so in this way we can look at devices as. Providing a sense of structure into the digital experience and the access into the software that we’re looking to provide. So with one thing that we can look at is how it fits the stakeholders needs. So all the stakeholders that come into the organization are going to have different needs for what they need to accomplish. And so we need to make sure that there is a good pairing between the data that they need to access and the device on which they are accessing that information. For example, if we were to send a sales Rep or a technician into the field, if we had a very complex app that they were to access on their phone. For a mobile device in the field, it can offer some headaches for them because the device itself might not match the way that the software is being rendered, the way that users are working with it. And so as subject can create a very poor experience. We want to make sure that whatever devices that users have or the way that we’re looking to have them access thing on devices, but it meets the needs of what they want to do and there can be a variety of ways of looking at this. It’s not just, you know. Stakeholders and or sales reps as stakeholders and them coming in and working with the organization, but even external stakeholders that might be interacting with the organization. For example, at some places like when you go to check in at an airport and work with an airline, they’re going to send you to a kiosk. That kiosk is effectively acting like a tablet and a kiosk or a desktop touch computer and a kiosk mode. And it’s because. Is able to render information in a way that presents it relatively better structure to the screen that it’s on and then that allows the users to be able to get just the data that they need, in this case checking in for their flight, adding additional bags if they need to and then getting their boarding pass. So we just really want to make sure that when we are building out the experience that we are aware of the different devices that users will bring and how the stakeholders. We’re expecting to work with the software and the company in that particular situation with the device that they’re on. And this can also get pretty tricky when we have very complex processes that need to be in place and users are accessing those on their phone because the phone as a mobile device might not be the best to allow that to happen. The other thing too that I want to stay here is devices might not also be an interface in some cases, depending on what the needs of the company are or the needs of the stakeholder. A device could also be a server, and a server is essentially a very powerful computer that is allowing us to host an application. But it can also be a way of regulating how users have access into that application, and it can also be a way of housing. Data and making sure that we’re able to provide and serve up that data when it’s needed. And so we just want to keep in mind that the stakeholders needs can encompass a variety of different applications and device types that would be needed to access those applications. The great part, and also one of the poor parts of devices is security. If we set up security properly on devices, then we can protect the company’s information. If we don’t set up that security properly, then we can open the door for users to easily access and act maliciously with company information and data. So we want to make sure that the devices that we’re putting information on that the security of those devices. Meets the requirements and needs of the organization. So what I mean by that is if you’re issuing laptops and devices to your users, that you want to make sure that you’re using something to mitigate the passwords that users are putting on those devices. So what that means is if a user were to say, have their laptop at Starbucks and they’re working away and they get up and go to the bathroom and they don’t put their laptop away or they don’t even lock the screen. Are there things in place that would then either protect the apps that are on that device? So maybe through a secondary set of like notifications or login parameters? Would the device itself lock after so much time of not being used? Would the user itself have some sort of requirements for the PIN or password that they need to put on for that device? So that’s the other thing too is even if we force passwords and force different types of logins to a device, users can. Find some interesting ways of getting around those parameters. They could do things like set up very easy passwords that make it so they don’t have to do anything complex in order to access and work with that device. The massive, massive downside is is that when that user leaves their laptop just open and about, somebody else is able to come in, guess that password, get into the device, and now depending on the other security parameters we have on that device, that user might have access to just about. Everything the company would need to do in order to access what’s going on. And so we want to make sure that we’re protecting things where we can and when we can. That way we can determine who has access to what and make sure the people who are accessing things are the ones we want to actually access them. And we also have to take into consideration that devices have the ability to connect with other things. And what this means is things like Wi-Fi. When the device is able to access different types of networks, people can come in and use those networks to get access into the devices and then act maliciously. Similar with things like Bluetooth and other types of ways of connecting devices. And people can just put in thumb drives or like a USB into a device and from there be able to compromise. Device and get access into the company’s information and data. So we want to look at what data we’re keeping on the devices, what the devices are being used for and what it is that we are or are not allowing them to connect to. For example, some companies will even go to such an extent that if they are working with other companies data that they will prevent any of those devices from accessing the Internet itself. And in these cases what they will likely set up is some sort of. Intranet. And with that intranet, they will set up different processes that prevent the devices from being able to connect to the outside world. So they will not be able to connect to the Internet. But so long as that device is within that physical area, so say within the building or whatever other way that it’s mitigated that it’s able to access the company’s information. And if it’s outside of that, then there’s not able to access the company’s information. So we really want to make sure. That the devices that we are issuing or the devices that are accessing our information that they fit the stakeholders needs and what the stakeholder is looking to do, that it’s secure and we have the security parameters in place and if need be that we’re monitoring and mitigating what types of connections and access that that device has to data all around. And in the next part we’ll get a bit more into the security aspects. Working with data.
Related Content
More Content
Create a professional and functional website with ease using online page builders. Explore factors like ease of use, customization, features, mobile responsiveness, SEO tools, support, and pricing to choose the right website builder for your needs.
Email marketing is a versatile and effective strategy that can be applied across industries to engage customers, drive sales, and build relationships. This article explores the application of email marketing in industries such as retail, healthcare,
Discover the power of content management solutions for your business. Effectively manage and streamline your content creation, organization, and distribution processes. Improve collaboration, enhance customer experiences, and boost productivity. Learn about the benefits, key features, and
In this comprehensive guide, we will delve into the intricacies of email marketing with click funnels, exploring the numerous benefits and strategies that can help businesses boost their conversion rates.
Content marketing involves writing and designing content to stand out from competitors. Read here to learn about the best tools for designing content.
Gain insights into the pivotal role of stakeholder perspectives in shaping digital experiences. Understand the significance of stakeholders’ concerns, skills, backgrounds, resources, desires, and networks in designing effective digital interactions. Tailoring digital experiences to align with
Explore the critical role of stakeholders in shaping a company’s digital experience. Understand internal and external stakeholders, navigate mixed stakeholder relationships, map stakeholder journeys, optimize device interactions, leverage software effectively, and harness the power of data.