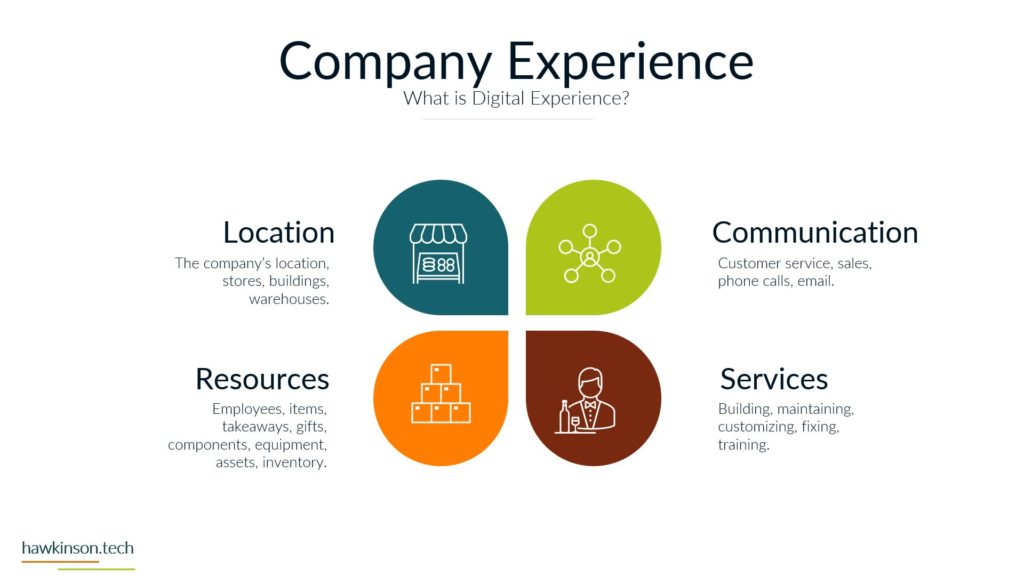
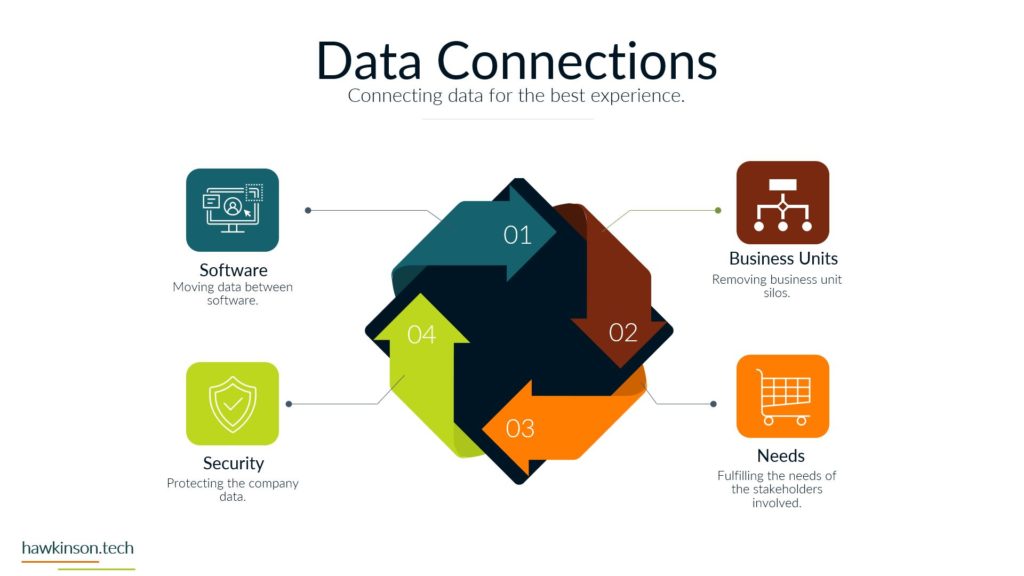
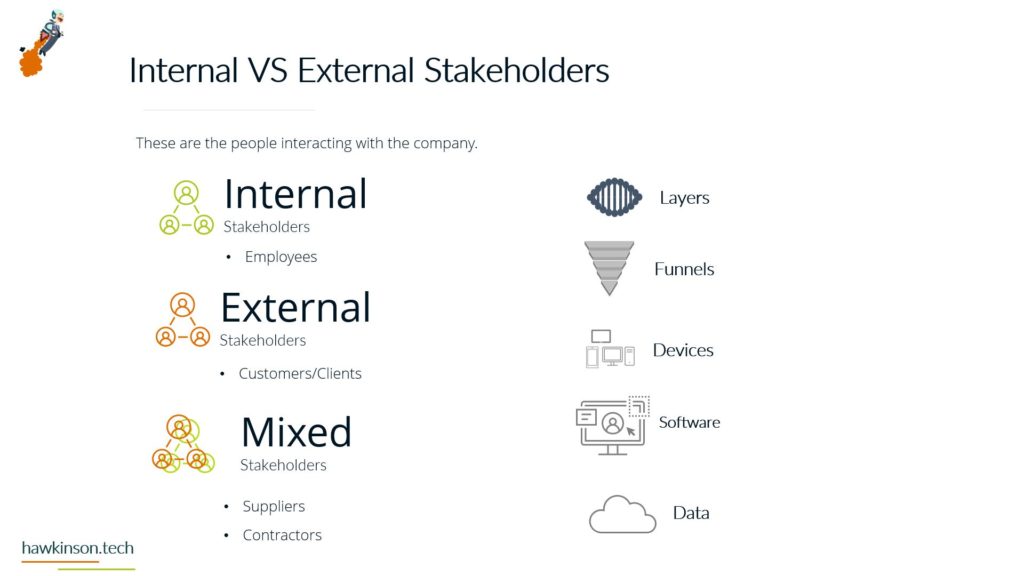
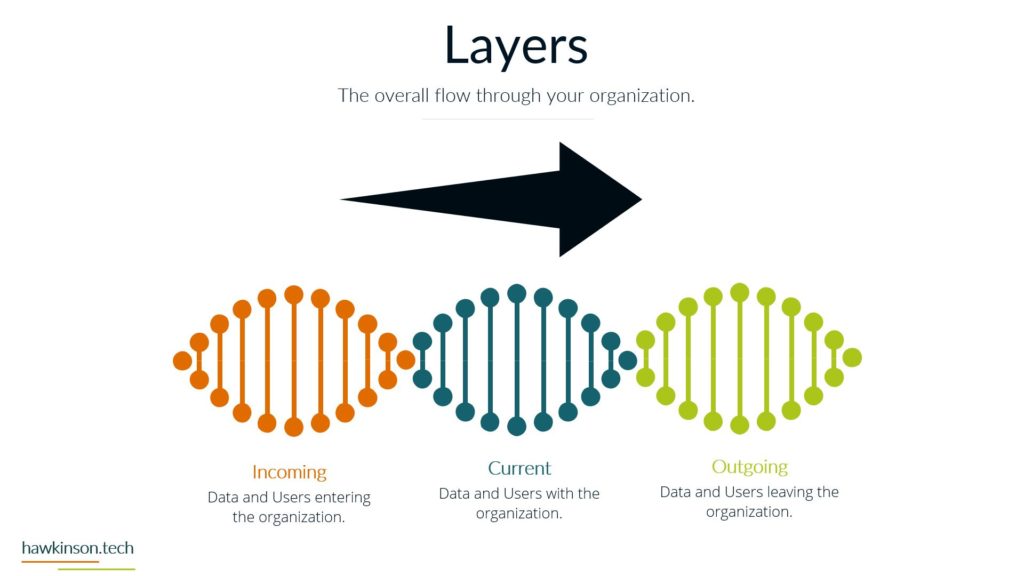
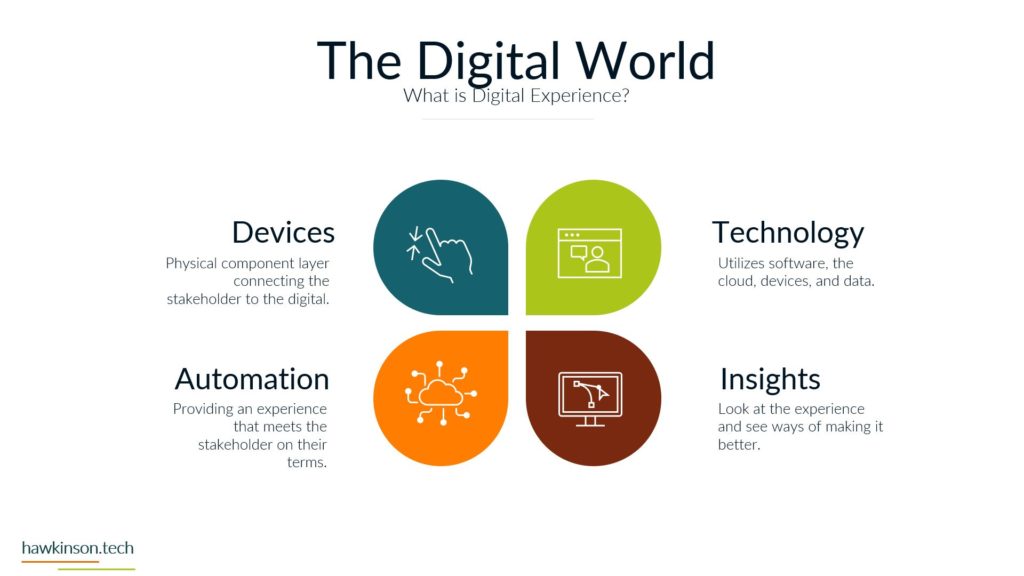
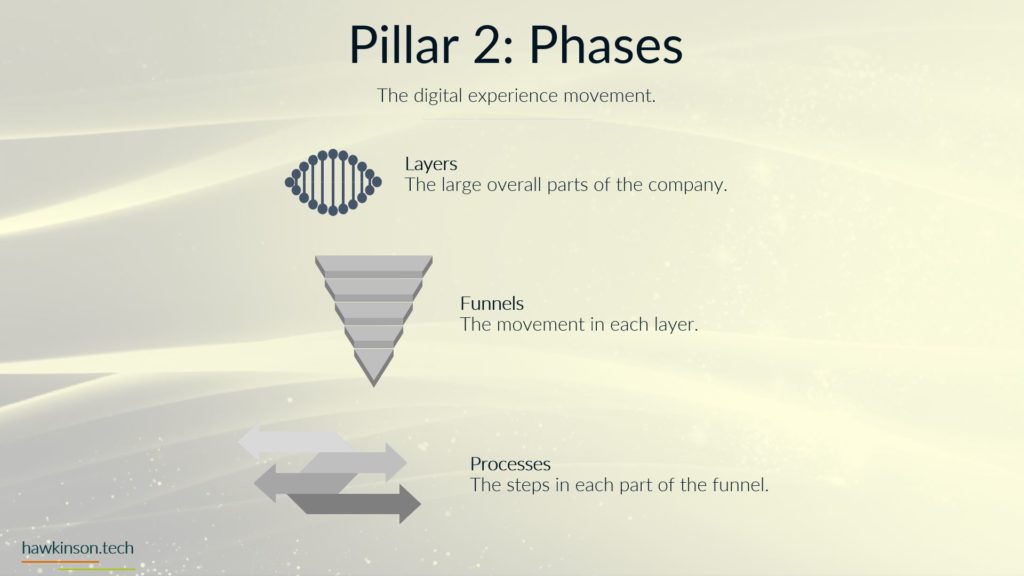
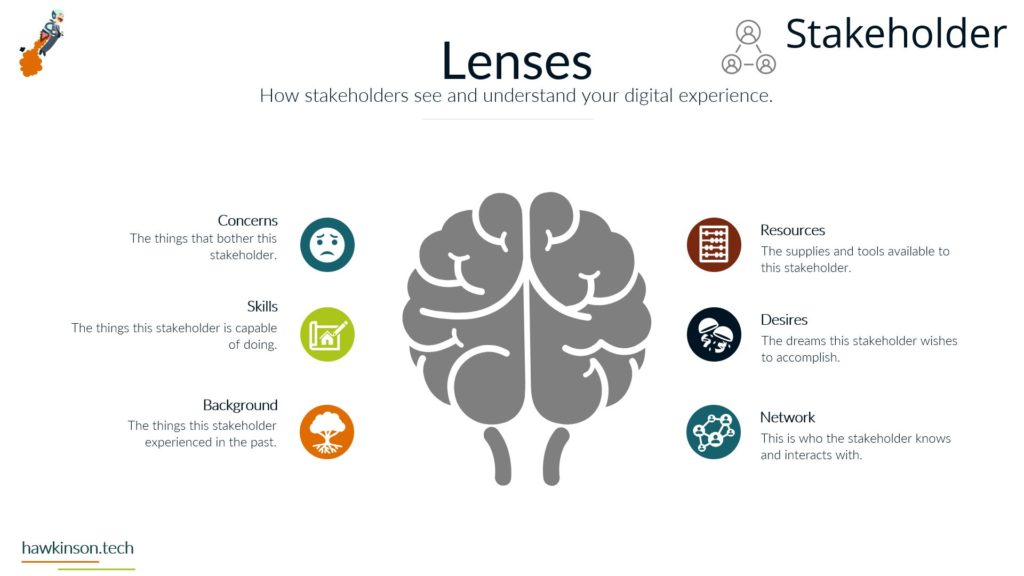
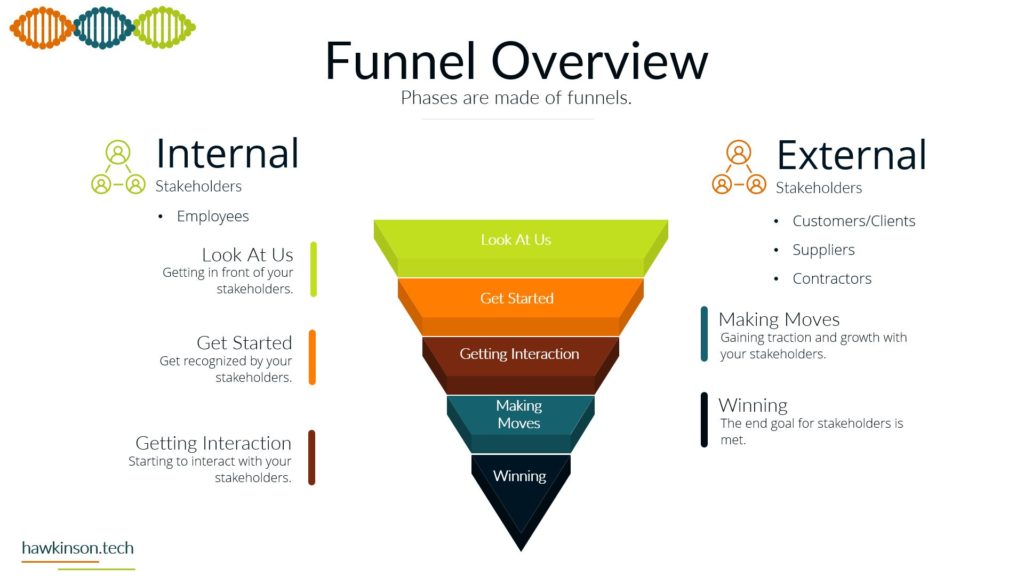
In this part, we look at devices used by stakeholders and how they impact a digital experience.
Digital Experience | Pillar 2 Phases | Lesson 4 Devices
Follow Me Elsewhere:
Play Video
Play Video
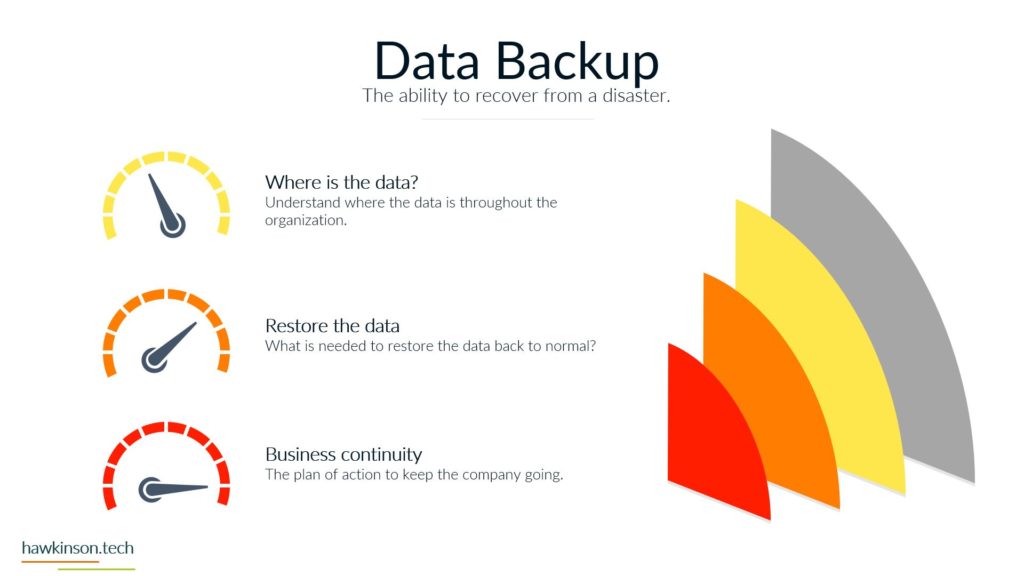
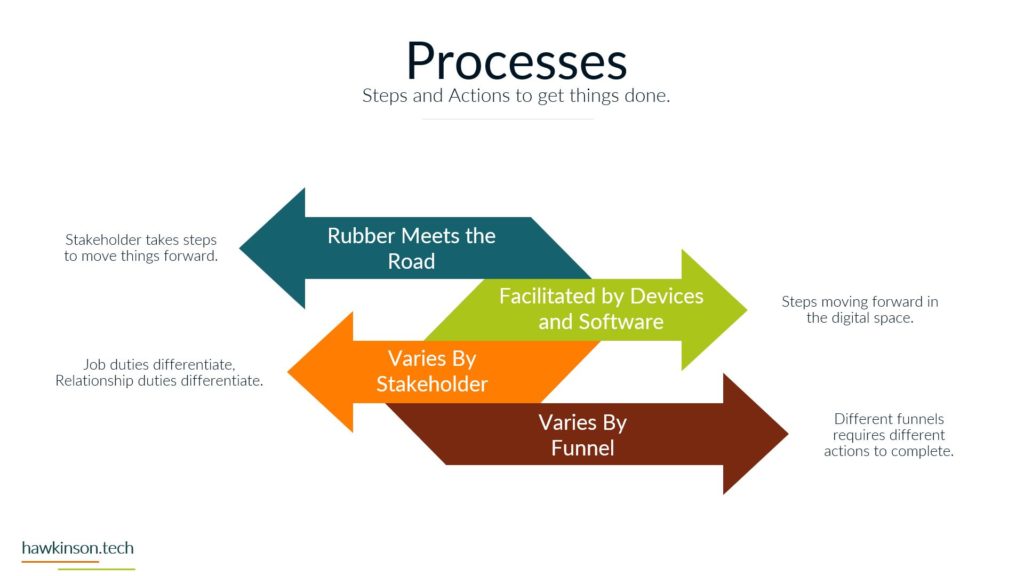
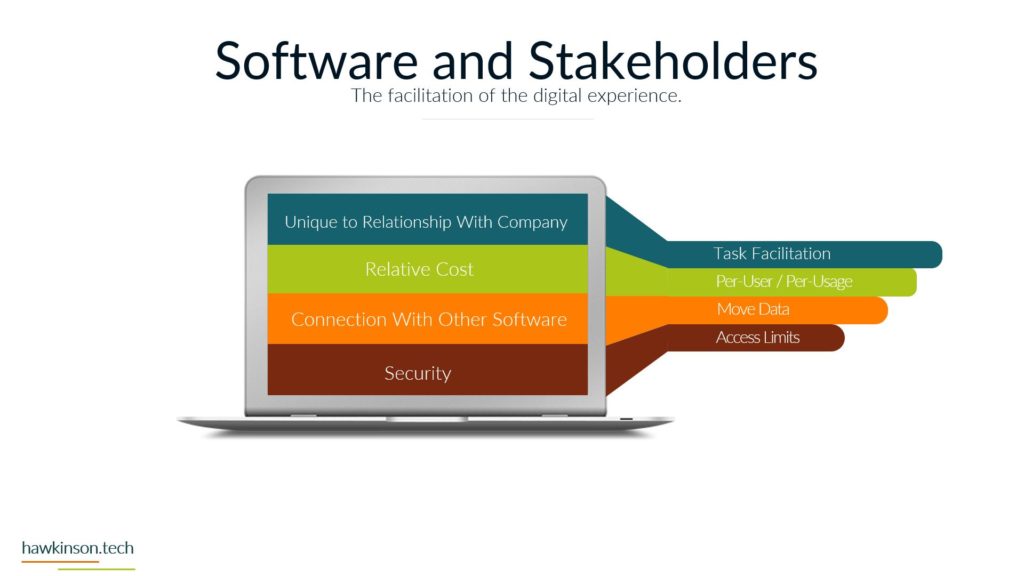
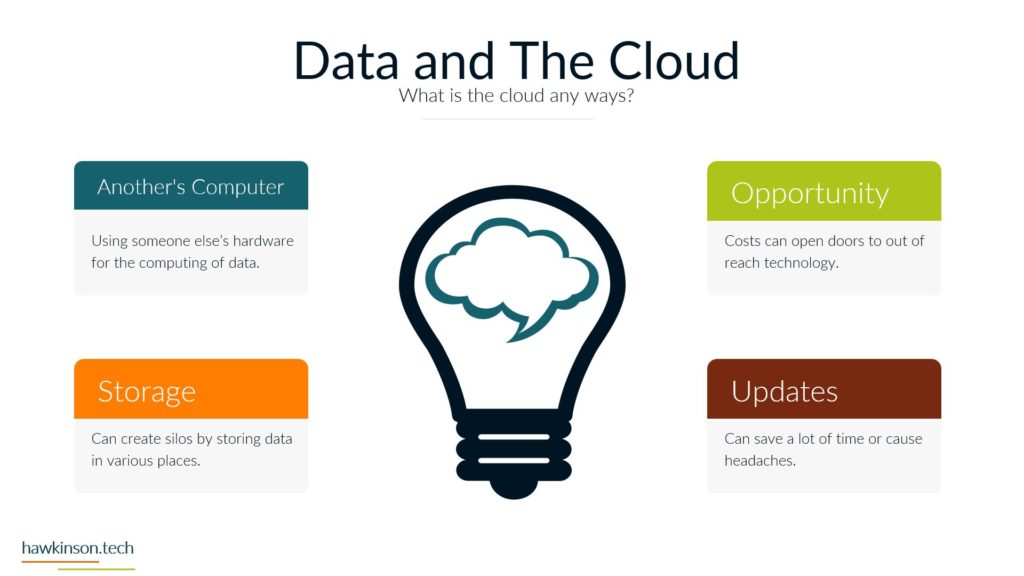
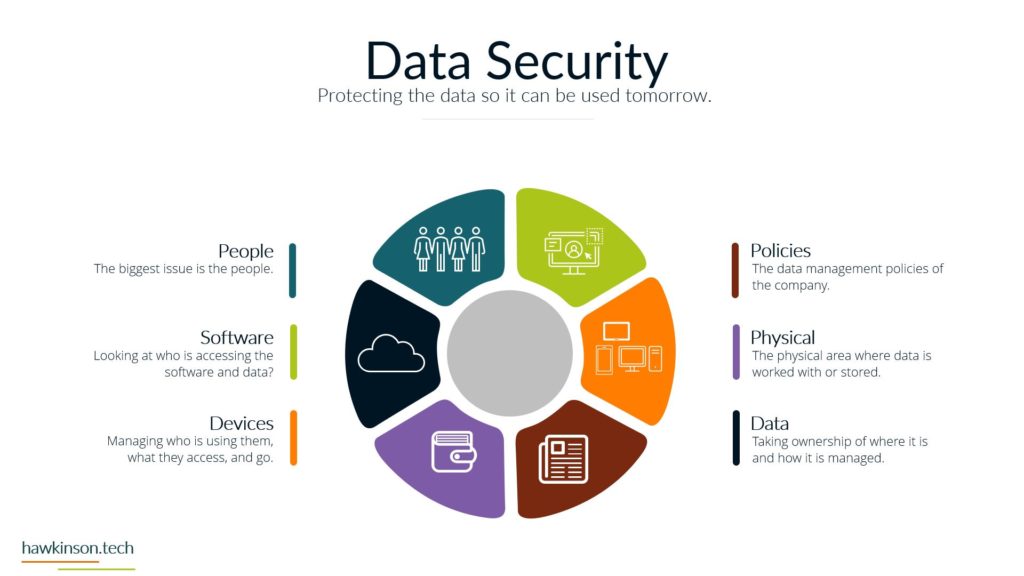
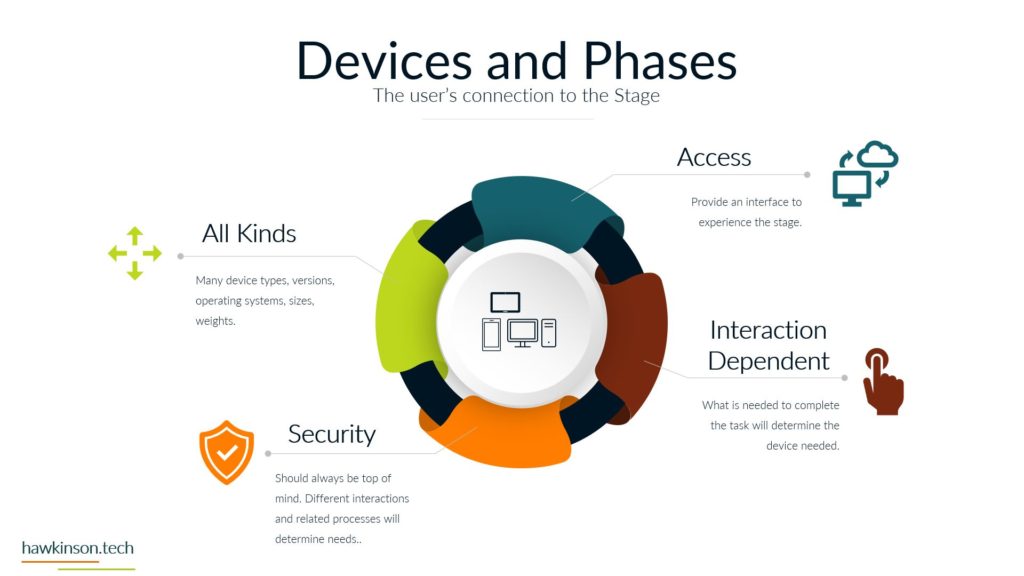
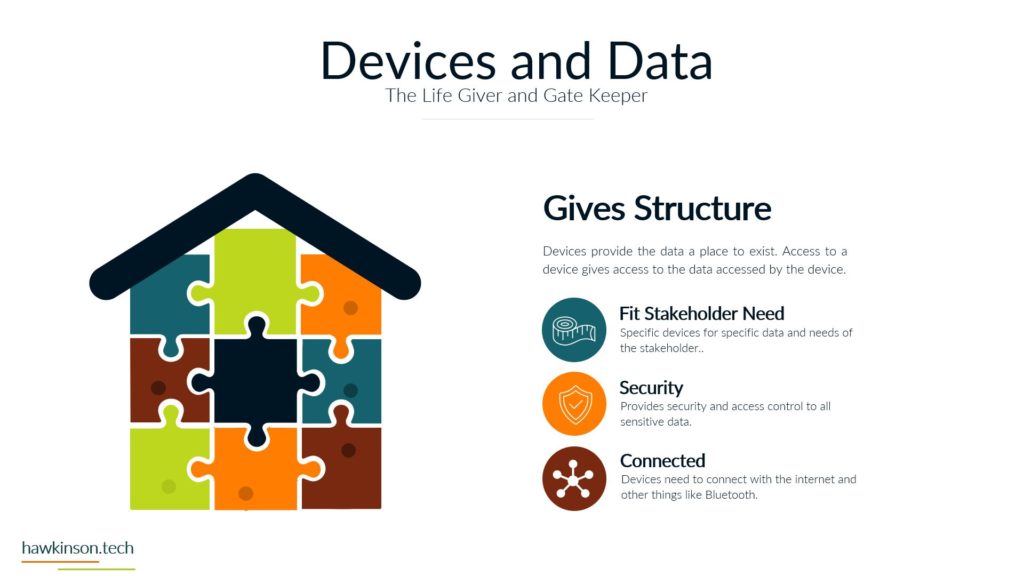
Now let’s take a look at the devices and how devices tie into our phases and how users work with them. So devices are an interesting kind of position here when we’re looking at some of these phases and our funnels. So for one, devices determine access. This is because all of the. Devices provide an interface for a user to be able to work with the data and the processes tied to that data and they’re able to access it in the digital world through devices. If we are looking at just a regular company experience, then essentially we would have you know, coming into the office or in a physical location or even a phone call in order to access these systems. But in our digital world, in our digital experience, we can regulate access through devices. We can do it with software as well and we’ll get to that, but for now just know that with our devices we can use them to determine access. The reason for this too is because, as we’ve talked about before, different devices and different device types provide different experiences, and so we need to account for that when we’re giving users devices or allowing those devices to access our systems. They’re definitely going to be interaction dependent and specially when we’re looking at things in the digital world, we need the device in order to actually make things happen. We need somebody to click on the computer or to click on their phone or tablet in order to move things to make things happen. So it’s very much a process that needs to happen on the device in order for things to move forward and the process to be fulfilled. We have security on devices that we need to be aware of. This security can be things like making sure that there’s passwords and that the device locks itself. The reason for this security is somebody can pick up a device and have access into your company system. So if you have desktops that don’t have passwords on them, or if you’ve issued users laptops and they’re able to take them wherever, if those devices aren’t secure, then you’re essentially opening up. For malicious users to have a way into the company, so then all somebody would need to do is just go and pick up that device and then they can use the interactions and get into the data. Get into company systems and that might not be at all what the company wants. Likewise with improper security, even the best of the intended users can access systems that you might not want them to access. See, not all users need to have access into. Everything that the company is doing or needing to see everything that the company is doing. And so by mitigating the security with the devices, we can not just protect the company from malicious actors, but we can also make sure that positive actors with the company are only accessing what it is that they need to access. And with that, there can be all different kinds of devices that come in contact. So as we said before, we have things like our bring your own device and needing to regulate those. We have company issued devices and needing to regulate those. All of those devices then have different versions depending on how the user is updating them. There’s different sizes of devices which can come into play depending on the application that you’re producing if your application works really well and is very data. Driven and tends to focus on desktop. Then you need to be aware of what happens when users access that on their phone. Wise, if they’re accessing things on tablets, um, the other side of it too is there’s also some devices that operate like kiosks. And so they’re designed to just kind of produce one app or to interface with one set of an app. And in these cases as well, we want to be aware of that and what it is that we’re allowing users to access and even again the security on that because at the same time even if you give, you know, say we have a public facing. That is acting as a kiosk. A savvy user might know what it takes to move that device out of the kiosk mode. And so if we’re not aware of that and we aren’t securing it properly, then essentially we could open up a public front that allows access into all of the company systems. So when we’re looking at the devices and our funnels and the different phases and processes, we want to be aware. Of the type of devices that users are using, the updates on those devices, the types of devices that they’re using, the security on those devices and what it is that they can access as they’re interacting with the company, the company’s data through those devices. And next we will move on to software and how software ties into some of these phases as well.
Related Content
More Content
If you want to take full advantage of SEO, you must learn and use keywords effectively. Here are 4 types of keywords you should know and use.
Read here to learn more about the world of email marketing, the email marketing definition, types of email marketing, its key concepts, benefits, and more.
Discover effective examples of email marketing campaigns that enhance engagement and drive conversions. Explore strategies like welcome email series, newsletter campaigns, abandoned cart emails, re-engagement campaigns, personalized recommendations, and seasonal/holiday campaigns. Learn how to nurture relationships,
eLearning has increased in popularity, and the demand for WordPress LMS options is high. Read here to learn about the best options for your eLearning platform.
A funnel builder is a piece of software or a platform that helps develop and manage sales funnels for organizations and marketers. A funnel builder frequently includes various features and tools, such as drag-and-drop editors, pre-built
Discover the best email marketing practices and strategies to create effective email campaigns. Learn the importance of personalized welcome messages, personalization tokens, and segmentation. Keep your CTAs above the fold for maximum impact and keep your
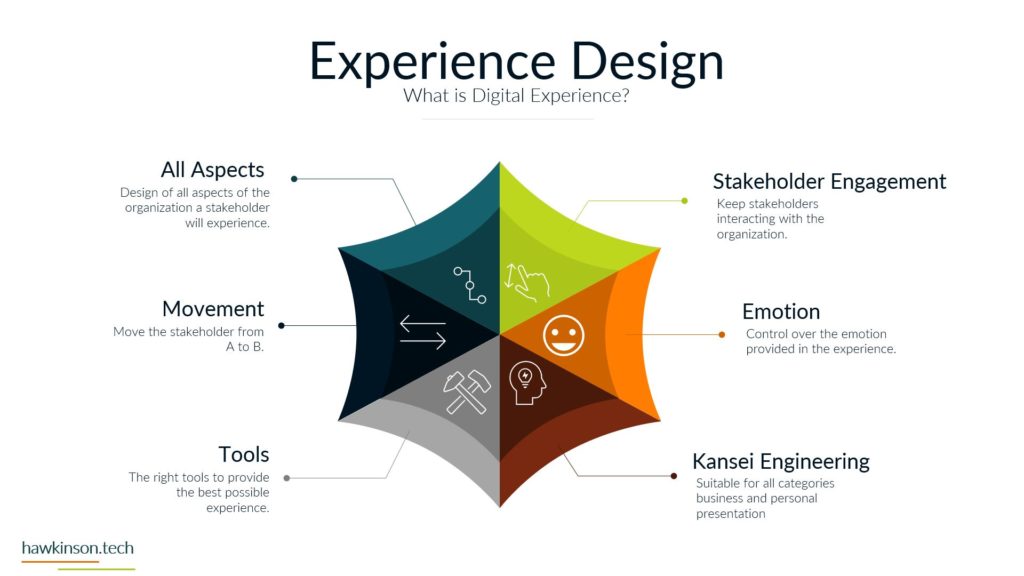
Experience design is a powerful process that involves configuring organizational components to achieve desired outcomes. This blog post explores the key aspects of experience design and its significance in creating exceptional company experiences. It covers tailoring
Discover how Learning Management Solutions (LMS) revolutionize corporate training and drive organizational success. Explore the benefits of enhanced accessibility, personalized learning paths, centralized content management, streamlined administration, and collaboration. Overcome implementation challenges and learn best practices