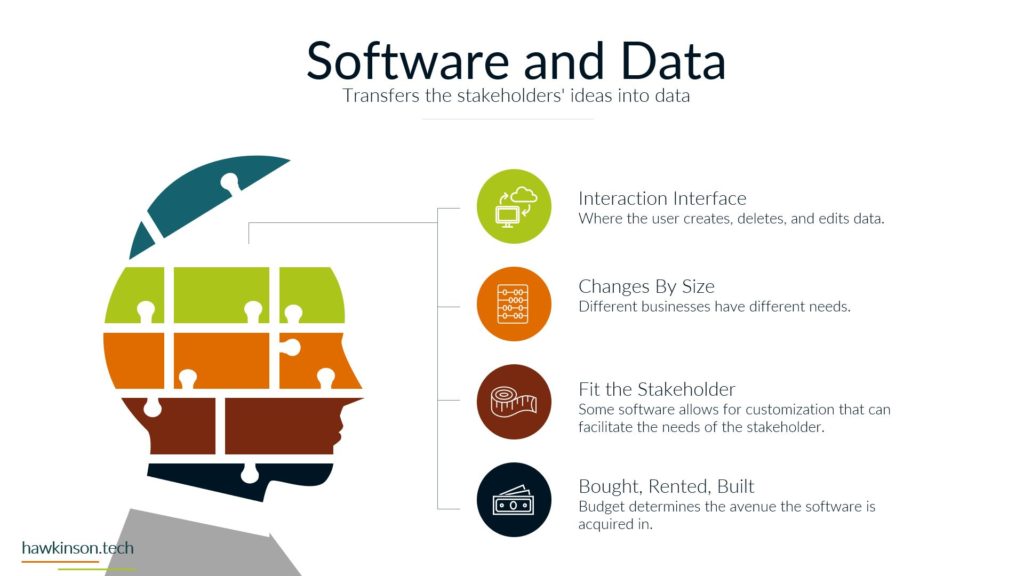
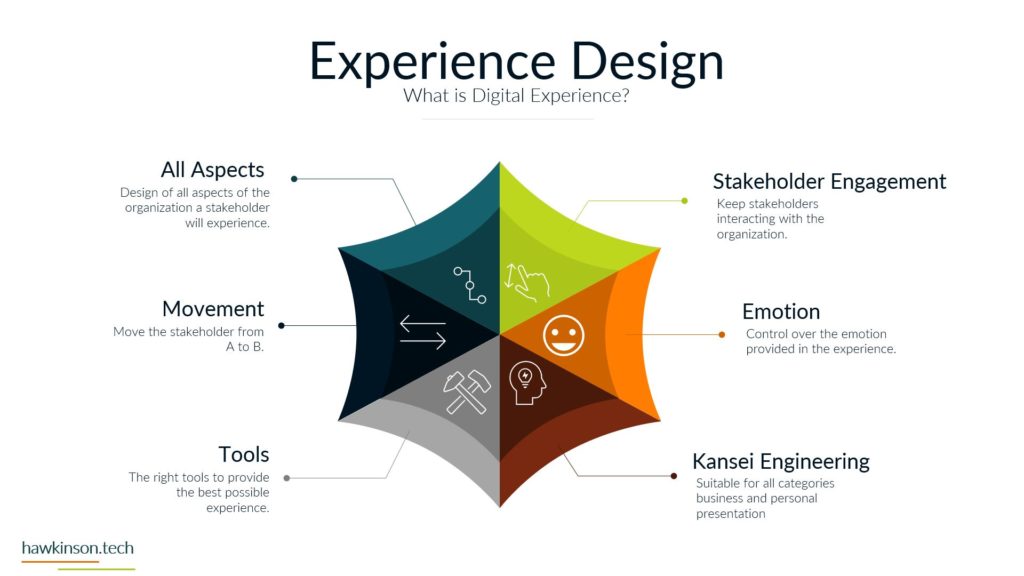
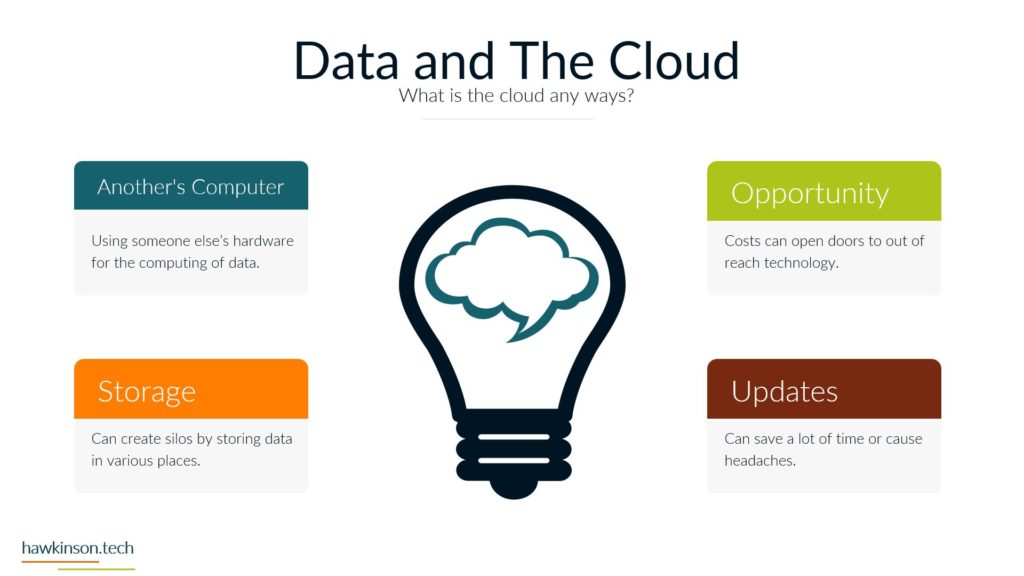
This lesson looks at data and its security impacts on a digital experience.
Digital Experience | Pillar 3 Data | Lesson 3 Data Security
Follow Me Elsewhere:
Play Video
Play Video
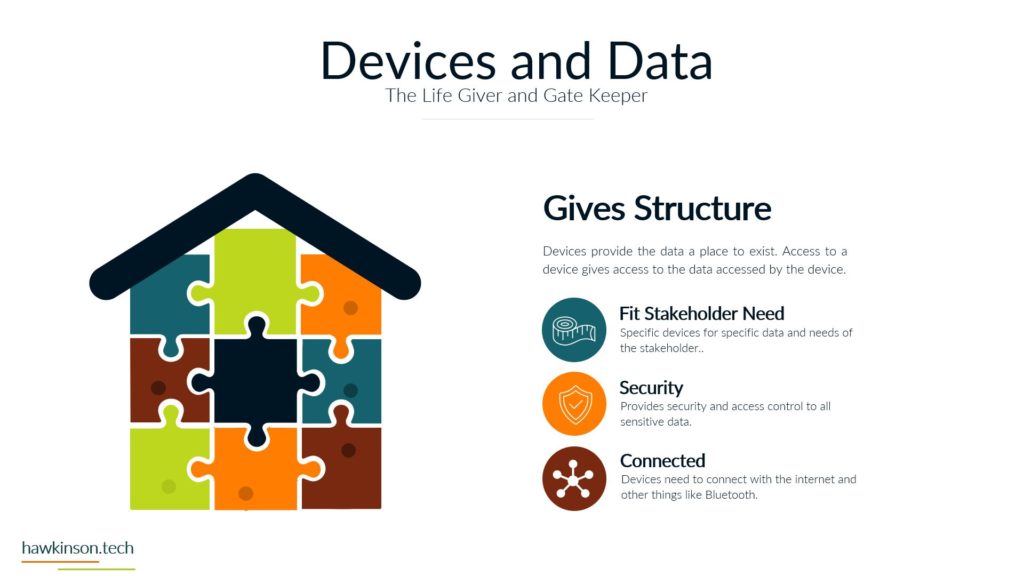
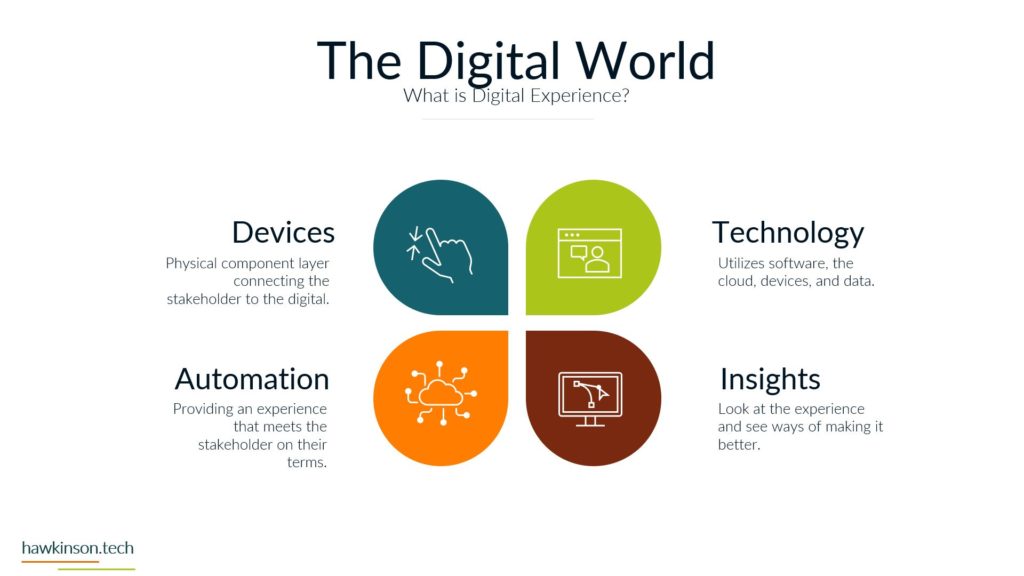
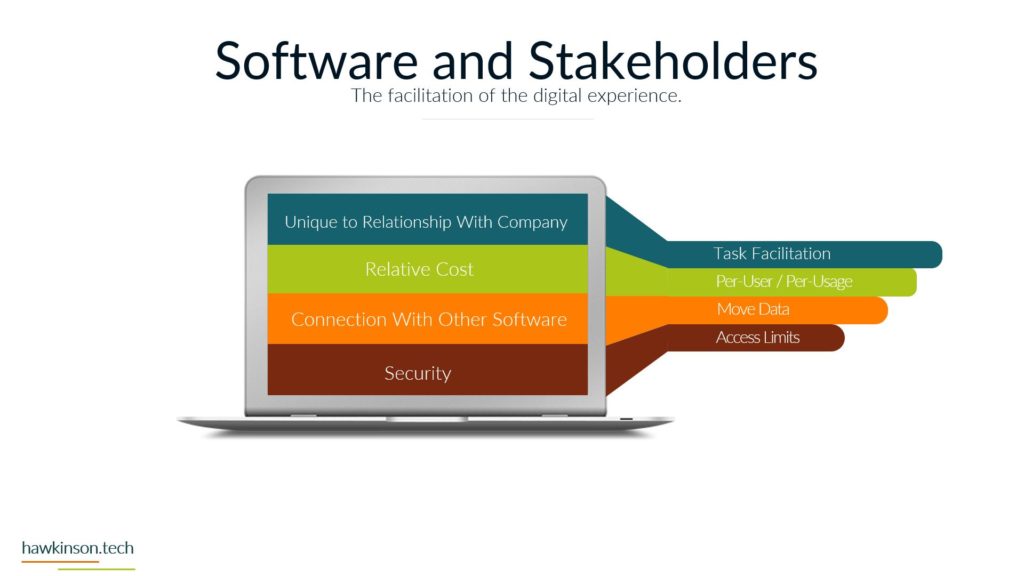
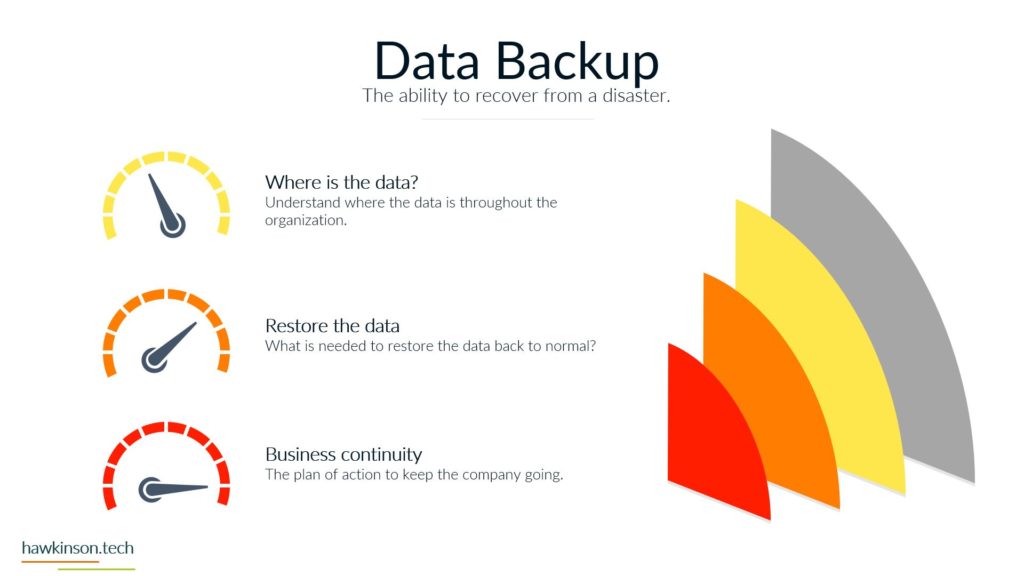
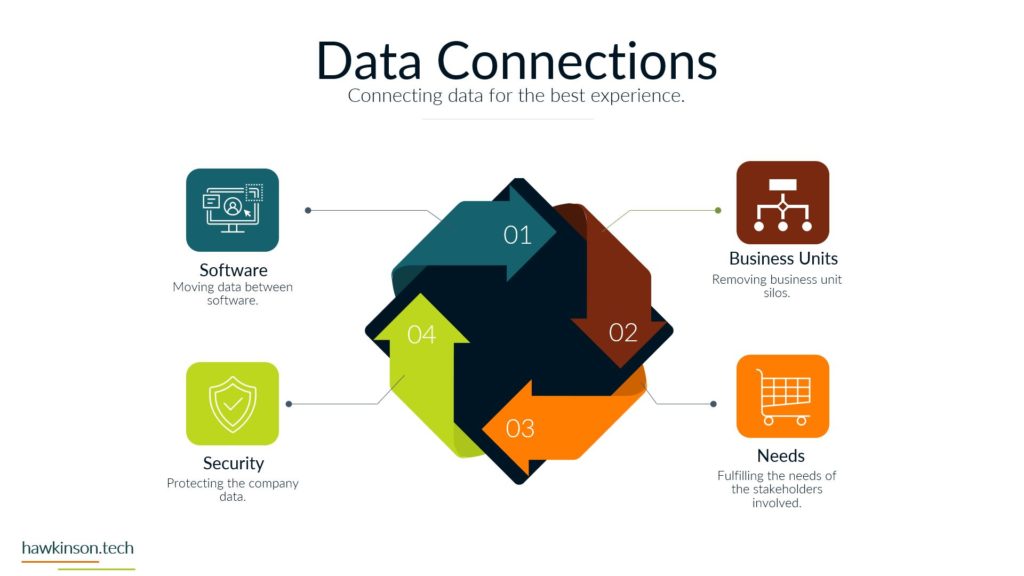
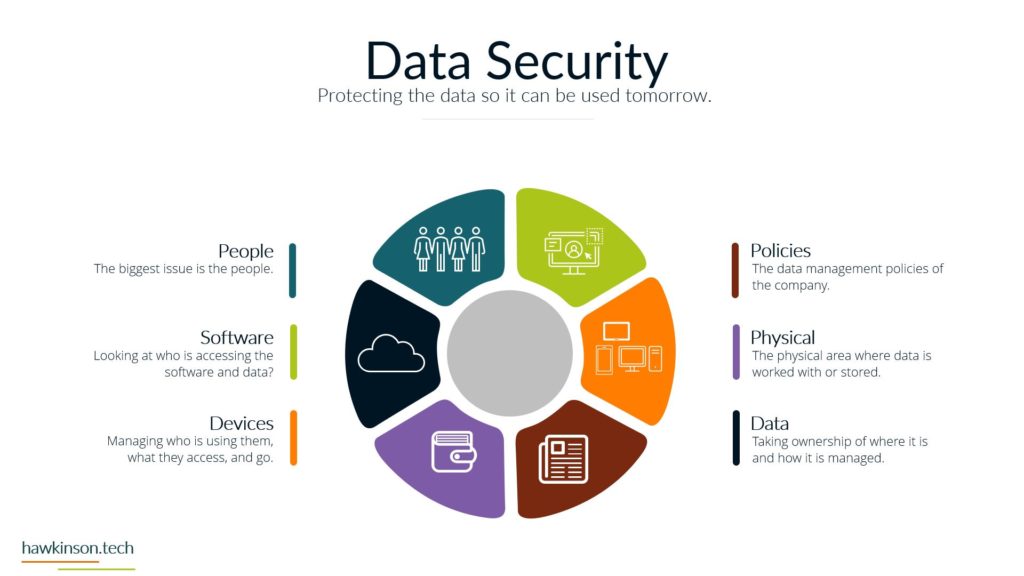
So let’s take a look now at data and security and some things to be aware of in our digital experience when it comes to just securing it and what that means. So the first one that might be surprising is people are the biggest security threat. The people that are accessing the information are essentially being trusted to not compromise. That information or to not provide their credentials, not share their credentials, not allow others to access things. But The thing is, is there’s ways to kind of deceive people. There’s different behavioral things that can be put in place that can make it easy to fish somebody. So we can kind of see this in certain call centers, for example, where people might call in and pretend to be like a supervisor or something like that, acting like they need to get access or the one that we see quite a bit. Whereas somebody gets an e-mail and need to send the CEO some credit cards or other things. And The thing is, is those malicious actors are looking to see who in the organization they can tiger target. Then they’re looking to see what kinds of situations they can set up. So then that way they can go in and essentially get that person to act thinking that they’re doing something positive and then take advantage of it. The other thing too. These people tend to develop habits like wanting to use weak passwords so that way they don’t have to go back and keep remembering passwords or having to reset them or use different passwords and that can also cause issues. If one of the users passwords gets compromised then that means whoever took that password could likely have access into the other accounts that are associated with that user. Which means that that that user can be a high target people at different levels in the organization. Are also likely to have different sets of attacks against them. So for example, people that are on say the frontline of a business, they may be in a position of getting you know, just very blanketed attacks to them versus people that are in a more executive type position might get very, very specific spear phishing attacks against them where they’re again trying to play off of the behaviors and setting up a situation to get somebody to essentially freely give up information. Without realizing it. So the biggest thing here too is just making sure that when you’re setting up processes and trying to secure things, that the people in the organization have the things that they need to be able to not compromise. So things like having password managers can make it so it’s harder for people to be compromised because then they’re, you know, having to have multiple, they’re not having to use the same password and multiple different accounts. They can instead have something where they technically need to remember just one password. But are able to store different passwords from all kinds of different places and be able to go back and use those efficiently. Software is another security concern. There’s different things that go into the software. So for one, access into the software, seeing who’s using it and why they’re using it. Users that don’t need to use software shouldn’t have access into it just because then you’re not having loose end credentials. You want to make sure that. People have the right permissions within that software so that they can only access the right things. Then there’s other things too, like seeing where the software is hosted. So one of the things that leads to a lot of websites and other kind of compromisation through those types of takeovers is that somebody will actually do some sort of phishing attack into the host of that software. It’s not even the people that design the software, but the people that are hosting it and giving it access to the Internet. They might get compromised. Which then gives somebody the ability to go in and take advantage of that and work with that and provide that into other things. And then they can, once they have access, for example, into one part of the software, then they can escalate themselves into other parts of the software and go from there to take advantage of the system and kind of work things that way. There’s other parameters of how the software itself is built and the security protocols in there. You know, there’s things like when somebody enters information into a password. Deal. Depending on how that password field looks at the characters and itemizes, the characters that were put in could allow somebody to essentially trick the software into thinking that they have access into everything. So if we’re not removing certain characters, or if we’re not updating the software, then it can lead to some of those security concerns. So again, updates is a big one, making sure that everything is up to date just because old legacy software can have holes in it where users have found those holes and then are able to. Go in and compromise accounts because of that. The next one is devices, which we’ve talked about making sure that whoever has access to a device is securing the device properly. So making sure that they have a password in it, that the password is of certain characters or a certain amount of characters can be ways to protect that. Making sure that when a user isn’t at the device that the device is effectively closed down or might require another password or pin to get into it just because if we have access into the device. And then we don’t have anything in place that’s securing the software on that device. Then that device becomes a massive gateway to open up a back door into the system. In addition, different devices if we as we’ve mentioned can house different types of data. So somebody that compromised the device and then had access into the software could look to even change that device into something else in the network. And then by changing that device into some other, you know, maybe like fake server essentially, then they can use that to try and escalate to other parts of the network. And take over the company or extract data from it. So one way we can protect those things is with policies, making sure that we’re managing the data properly. Making sure that if we do have something that is overlooking the devices or overlooking the software that it’s managing what kinds of passwords users are putting in there, it might be managing the access that they have into that software. And when if something is a very, very sensitive piece of software or a very, very sensitive device that has access to the software. Then we might set up policies that will go through and eliminate or make it harder for somebody to access that. So we could do things like make it so somebody only has access to certain software at certain times, or maybe they have to ask for permission to get into that software before they can do anything else with it. So there’s just other ways that we can mitigate security and protect the data in the organization by setting up proper policies. Now, the other thing too, when it comes to policies is not just. Making sure that we have other software that’s regulating access and regulating passwords. But even just the companies mentality, you know, how does the company see software? How does the company look at data protection and just having internal policies that way? For example, if the company is open to allowing users to share passwords and credentials then that can open up the door for an attack. But if there’s companies or if there’s policies in place and there’s SOP’s in place to prevent that from happening and. You know, have some sort of punishment or something that goes to the user. If they were to share their passwords or their credentials, then those policies can also help to mitigate that and protect the company from some sort of malicious attack. Physical and the parameters of what’s going on in a location is another thing to keep in mind. You see somebody who might pretend to come into your office building, let’s say, pretending to maybe be a maintenance worker, but from there they could do things like set down a USB drive, and then somebody could plug that USB drive into their computer and compromise the company. So we want to make sure that we’re locking down physical locations. We want to make sure that anybody who has access into a physical location. That could lead to working with sensitive data doesn’t have the ability to just go in there, you know, as they freely want to want to make sure that it’s regulated in some way. And again, that can come down to different policies, who has access into what and what. But it can be something that gets vastly overlooked when you’re looking at, you know, data, because we’re usually talking about software and computers. So thinking that the physical environment can compromise it is something we usually don’t think of, but it’s something that very well. Another part of physical is outside of the office, if users are taking their devices and they’re accessing systems that would be on like public Wi-Fi. So they might have a secure, you know, device, but then they go into a Wi-Fi situation on a public network and try to access system information or company information and that could then lead to compromise. So we want to make sure too that if users are taking devices into physical locations outside of the office, how are we regulating that? And again, what kind of policies do we have in place around that? And what this is, is it all comes down to the data. We want to make sure that we are taking ownership of where the data is. Who has access to the data? When can they access the data? How can they access the data? What parameters do we have in place? If somebody does have something happen with data or do we do things to temporarily mitigate people’s access into data and all of these things then come back down to our policies, they come back down to the devices that we’re issuing, comes down to the software. And back to the first part, where we’re back to the people and how their mentality is and using these different systems, what they believe is safe versus what they don’t believe is safe. And even just their training in general, training the people to make sure that when they’re accessing data that they’re respectful of it, that they’re not just looking to, you know, just access the data and just get it out there freely, but that they’re willing to actually protect it and protect the company at the same time. So next we’re going to get into data backup and what that means for our digital experience.
Related Content
More Content
Discover the power of no-code and low-code tools for building complex dynamic websites. Explore popular options like Elementor, Divi, Advanced Custom Fields, Crocoblock, Meta Box, and Toolset to create visually stunning and interactive websites without extensive
Email marketing is one of the most effective digital tools. Here are a few essential features to look for when choosing email marketing software.
A dependable CRM solution can streamline many tasks of your daily business. Have a look at the must-have features of CRM solutions.
The productivity application suite is a collection of programs intended to boost productivity and effectiveness at work. Examples of productivity application suites are applications for word processing, graphics, presentations, email, calendaring, and other tasks.
Revolutionize your business with the Digital Experience Foundations course, exploring the synergy between the digital world and the experience economy. Discover transformative opportunities and harness technology to create exceptional user experiences. Learn to invest resources wisely,
Video for the 5 Step Personal Branding and SEO Action Plan how to guide.
Discover five free tools that will take your email marketing campaigns to the next level. From AI-powered personalization to deliverability tools, these platforms offer features to optimize your email content, improve deliverability, and increase engagement. Whether